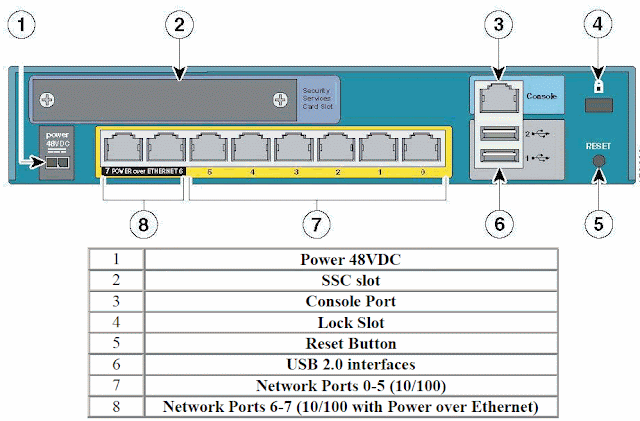
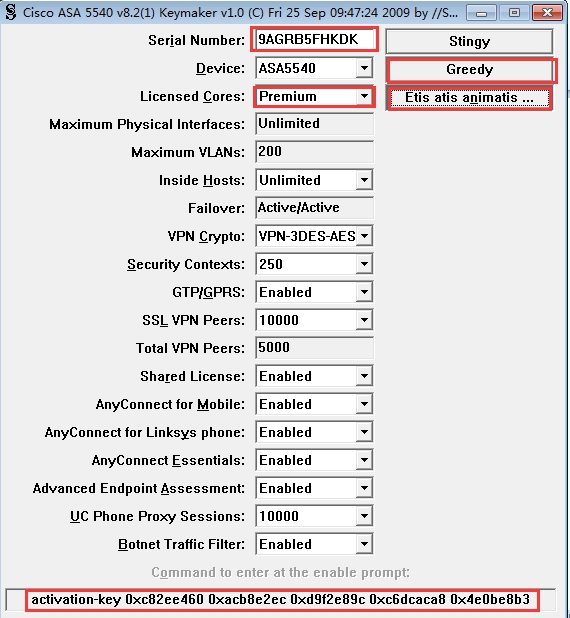
Cisco Asa 5505 Key Generator
The US-CERT Cyber Security Bulletin provides a summary of new vulnerabilities that have been recorded by the (NIST) (NVD) in the past week. The NVD is sponsored by the (DHS) (NCCIC) / (US-CERT). For modified or updated entries, please visit the, which contains historical vulnerability information. The vulnerabilities are based on the vulnerability naming standard and are organized according to severity, determined by the (CVSS) standard. The division of high, medium, and low severities correspond to the following scores: • - Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 - 10.0 • - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 - 6.9 • - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 - 3.9 Entries may include additional information provided by organizations and efforts sponsored by US-CERT. This information may include identifying information, values, definitions, and related links. Patch information is provided when available.
Please note that some of the information in the bulletins is compiled from external, open source reports and is not a direct result of US-CERT analysis. High Vulnerabilities Primary Vendor -- Product Description Published CVSS Score Source & Patch Info adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable buffer overflow / underflow vulnerability in the Primetime TVSDK that supports customizing ad information. Successful exploitation could lead to arbitrary code execution. 2017-03-14 adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable memory corruption vulnerability in the Primetime TVSDK API functionality related to timeline interactions.
Successful exploitation could lead to arbitrary code execution. 2017-03-14 adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable memory corruption vulnerability in the Primetime TVSDK functionality related to hosting playback surface. Successful exploitation could lead to arbitrary code execution.
2017-03-14 adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability related to garbage collection in the ActionScript 2 VM. Successful exploitation could lead to arbitrary code execution. 2017-03-14 adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability in the ActionScript2 TextField object related to the variable property. Successful exploitation could lead to arbitrary code execution. 2017-03-14 adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability related to an interaction between the privacy user interface and the ActionScript 2 Camera object. Successful exploitation could lead to arbitrary code execution. 2017-03-14 alienvault -- ossim The logcheck function in session.inc in AlienVault OSSIM before 5.3.1, when an action has been created, and USM before 5.3.1 allows remote attackers to bypass authentication and consequently obtain sensitive information, modify the application, or execute arbitrary code as root via an 'AV Report Scheduler' HTTP User-Agent header.
Release Notes for the Cisco ASA Series, Version 9.1(x) First Published: December 3, 2012 Last Updated: March 30, 2017. This document contains release information for.
2017-03-15 apache -- struts The Jakarta Multipart parser in Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1 mishandles file upload, which allows remote attackers to execute arbitrary commands via a #cmd= string in a crafted Content-Type HTTP header, as exploited in the wild in March 2017. 2017-03-10 azure_dex -- data_expert_ultimate In Azure Data Expert Ultimate 2.2.16, the SMTP verification function suffers from a buffer overflow vulnerability, leading to remote code execution. The attack vector is a crafted SMTP daemon that sends a long 220 (aka 'Service ready') string. 2017-03-10 bitlbee -- bitlbee Use-after-free vulnerability in bitlbee-libpurple before 3.5 allows remote servers to cause a denial of service (crash) or possibly execute arbitrary code by causing a file transfer connection to expire. 2017-03-14 bitlbee -- bitlbee-libpurple bitlbee-libpurple before 3.5.1 allows remote attackers to cause a denial of service (NULL pointer dereference and crash) and possibly execute arbitrary code via a file transfer request for a contact that is not in the contact list. NOTE: this vulnerability exists because of an incomplete fix for CVE-2016-10189.
2017-03-14 cambium_networks -- cnpilot_r200_series_firmware On Cambium Networks cnPilot R200/201 devices before 4.3, there is a vulnerability involving the certificate of the device and its RSA keys, aka RBN-183. 2017-03-10 embedthis -- goahead A command-injection vulnerability exists in a web application on a custom-built GoAhead web server used on Foscam, Vstarcam, and multiple white-label IP camera models. The mail-sending form in the mail.htm page allows an attacker to inject a command into the receiver1 field in the form; it will be executed with root privileges. 2017-03-13 f-secure -- software_updater F-Secure Software Updater 2.20, as distributed in several F-Secure products, downloads installation packages over plain http and does not perform file integrity validation after download.
Man-in-the-middle attackers can replace the file with their own executable which will be executed under the SYSTEM account. Note that when Software Updater is configured to install updates automatically, it checks if the downloaded file is digitally signed by default, but does not check the author of the signature. When running in manual mode (default), no signature check is performed. 2017-03-11 imagemagick -- imagemagick Memory leak in the IsOptionMember function in MagickCore/option.c in ImageMagick before 6.9.2-2, as used in ODR-PadEnc and other products, allows attackers to trigger memory consumption. 2017-03-14 imagemagick -- imagemagick The gnuplot delegate functionality in ImageMagick before 6.9.4-0 and GraphicsMagick allows remote attackers to execute arbitrary commands via unspecified vectors. 2017-03-15 libgd -- libgd Integer underflow in the _gdContributionsAlloc function in gd_interpolation.c in the GD Graphics Library (aka libgd) before 2.2.4 allows remote attackers to have unspecified impact via vectors related to decrementing the u variable. 2017-03-15 logback -- logback QOS.ch Logback before 1.2.0 has a serialization vulnerability affecting the SocketServer and ServerSocketReceiver components.
2017-03-13 microsoft -- edge A remote code execution vulnerability exists when Microsoft Edge improperly accesses objects in memory. The vulnerability could corrupt memory in a way that enables an attacker to execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
If the current user is logged on with administrative user rights, an attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. 2017-03-16 microsoft -- internet_explorer The scripting engine in Microsoft Internet Explorer 9 through 11 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka 'Scripting Engine Memory Corruption Vulnerability.'
This vulnerability is different from that described in CVE-2017-0130. 2017-03-16 microsoft -- internet_explorer Microsoft Internet Explorer 9 through 11 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka 'Internet Explorer Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0018 and CVE-2017-0037.
2017-03-16 microsoft -- server_message_block The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka 'Windows SMB Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0144, CVE-2017-0145, CVE-2017-0146, and CVE-2017-0148.
2017-03-16 microsoft -- server_message_block The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka 'Windows SMB Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0143, CVE-2017-0145, CVE-2017-0146, and CVE-2017-0148. 2017-03-16 microsoft -- server_message_block The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka 'Windows SMB Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0143, CVE-2017-0144, CVE-2017-0146, and CVE-2017-0148. 2017-03-16 microsoft -- server_message_block The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka 'Windows SMB Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, and CVE-2017-0148. 2017-03-16 microsoft -- server_message_block The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via crafted packets, aka 'Windows SMB Remote Code Execution Vulnerability.'
This vulnerability is different from those described in CVE-2017-0143, CVE-2017-0144, CVE-2017-0145, and CVE-2017-0146. 2017-03-16 microsoft -- windows_10 The PDF library in Microsoft Edge; Windows 8.1; Windows Server 2012 and R2; Windows RT 8.1; and Windows 10, 1511, and 1607 allows remote attackers to execute arbitrary code via a crafted PDF file, aka 'Microsoft PDF Remote Code Execution Vulnerability.'
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0084, CVE-2017-0086, CVE-2017-0087, CVE-2017-0088, CVE-2017-0089, and CVE-2017-0090. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0083, CVE-2017-0084, CVE-2017-0087, CVE-2017-0088, CVE-2017-0089, and CVE-2017-0090.
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0083, CVE-2017-0084, CVE-2017-0086, CVE-2017-0088, CVE-2017-0089, and CVE-2017-0090. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Windows Uniscribe Remote Code Execution Vulnerability.'
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0083, CVE-2017-0084, CVE-2017-0086, CVE-2017-0087, CVE-2017-0088, and CVE-2017-0090. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0083, CVE-2017-0084, CVE-2017-0086, CVE-2017-0087, CVE-2017-0088, and CVE-2017-0089. 2017-03-16 mikrotik -- router_hap_lite_firmware The MikroTik Router hAP Lite 6.25 has no protection mechanism for unsolicited TCP ACK packets in the case of a fast network connection, which allows remote attackers to cause a denial of service (CPU consumption) by sending many ACK packets. After the attacker stops the exploit, the CPU usage is 100% and the router requires a reboot for normal operation.
2017-03-12 novell -- iprint Remote attackers can use the iPrint web-browser ActiveX plugin in Novell iPrint Client before 5.42 for Windows XP/Vista/Win7 to execute code by overflowing the 'name' parameter. 2017-03-11 oneplus -- oxygenos An issue was discovered in OxygenOS before 4.0.3 for OnePlus 3 and 3T. The attacker can persistently make the (locked) bootloader start the platform with dm-verity disabled, by issuing the 'fastboot oem disable_dm_verity' command. Having dm-verity disabled, the kernel will not verify the system partition (and any other dm-verity protected partition), which may allow for persistent code execution and privilege escalation.
2017-03-12 oneplus -- oxygenos OxygenOS before version 4.0.2, on OnePlus 3 and 3T, has two hidden fastboot oem commands (4F500301 and 4F500302) that allow the attacker to lock/unlock the bootloader, disregarding the 'OEM Unlocking' checkbox, without user confirmation and without a factory reset. This allows for persistent code execution with high privileges (kernel/root) with complete access to user data. 2017-03-12 pharos -- popup An exploitable buffer overflow exists in the psnotifyd application of the Pharos PopUp printer client version 9.0. A specially crafted packet can be sent to the victim's computer and can lead to a heap based buffer overflow resulting in remote code execution. This client is always listening, has root privileges, and requires no user interaction to exploit. 2017-03-10 pharos -- popup A buffer overflows exists in the psnotifyd application of the Pharos PopUp printer client version 9.0. A specially crafted packet can be sent to the victim's computer and can lead to a heap based buffer overflow resulting in potential remote code execution.
This client is always listening, has root privileges, and requires no user interaction to exploit. 2017-03-10 pharos -- popup A buffer overflows exists in the psnotifyd application of the Pharos PopUp printer client version 9.0. A specially crafted packet can be sent to the victim's computer and can lead to a heap based buffer overflow resulting in potential remote code execution.
This client is always listening, has root privileges, and requires no user interaction to exploit. 2017-03-10 trend_micro -- endpoint_sensor Trend Micro Endpoint Sensor 1.6 before b1290 has a DLL hijacking vulnerability that allows remote attackers to execute arbitrary code, aka Trend Micro Vulnerability Identifier 2015-0208. 2017-03-10 trendmicro -- interscan_messaging_security_virtual_appliance An issue was discovered in Trend Micro InterScan Messaging Security (Virtual Appliance) 9.1-1600.
An authenticated user can execute a terminal command in the context of the web server user (which is root). Besides, the default installation of IMSVA comes with default administrator credentials. The saveCert.imss endpoint takes several user inputs and performs blacklisting. After that, it uses them as arguments to a predefined operating-system command without proper sanitization.
However, because of an improper blacklisting rule, it's possible to inject arbitrary commands into it. 2017-03-14 trendnet -- tew-812dru_firmware Buffer overflow in Broadcom ACSD allows remote attackers to execute arbitrary code via a long string to TCP port 5916. This component is used on routers of multiple vendors including ASUS RT-AC66U and TRENDnet TEW-812DRU. 2017-03-14 umn -- mapserver Stack-based buffer overflow in MapServer before 6.0.6, 6.2.x before 6.2.4, 6.4.x before 6.4.5, and 7.0.x before 7.0.4 allows remote attackers to cause a denial of service (crash) or execute arbitrary code via vectors involving WFS get feature requests.
2017-03-15 zammad -- zammad An issue was discovered in Zammad before 1.0.4, 1.1.x before 1.1.3, and 1.2.x before 1.2.1. Attackers can login with the hashed password itself (e.g., from the DB) instead of the valid password string. 2017-03-13 zammad -- zammad An issue was discovered in Zammad before 1.0.4, 1.1.x before 1.1.3, and 1.2.x before 1.2.1, caused by lack of a protection mechanism involving HTTP Access-Control headers. To exploit the vulnerability, an attacker can send cross-domain requests directly to the REST API for users with a valid session cookie and receive the result. Medium Vulnerabilities Primary Vendor -- Product Description Published CVSS Score Source & Patch Info adobe -- flash_player Adobe Flash Player versions 24.0.0.221 and earlier have a vulnerability in the random number generator used for constant blinding. Successful exploitation could lead to information disclosure. 2017-03-14 adobe -- shockwave_player Adobe Shockwave versions 12.2.7.197 and earlier have an insecure library loading (DLL hijacking) vulnerability.
Successful exploitation could lead to escalation of privilege. 2017-03-14 apache -- tomcat An information disclosure issue was discovered in Apache Tomcat 8.5.7 to 8.5.9 and 9.0.0.M11 to 9.0.0.M15 in reverse-proxy configurations. Http11InputBuffer.java allows remote attackers to read data that was intended to be associated with a different request. 2017-03-14 appneta -- tcpreplay Buffer overflow in the tcpcapinfo utility in Tcpreplay before 4.2.0 Beta 1 allows remote attackers to have unspecified impact via a pcap file with an over-size packet. 2017-03-15 artifex -- mupdf Buffer overflow in the main function in jstest_main.c in Mujstest in Artifex Software, Inc. MuPDF before 1.10 allows remote attackers to cause a denial of service (out-of-bounds write) via a crafted file. 2017-03-16 artifex -- mupdf Buffer overflow in the my_getline function in jstest_main.c in Mujstest in Artifex Software, Inc.
MuPDF before 1.10 allows remote attackers to cause a denial of service (out-of-bounds write) via a crafted file. 2017-03-16 artifex -- mupdf Stack-based buffer overflow in jstest_main.c in mujstest in Artifex Software, Inc. MuPDF 1.10a allows remote attackers to have unspecified impact via a crafted image.
2017-03-15 audiofile -- audiofile Heap-based buffer overflow in the MSADPCM::initializeCoefficients function in MSADPCM.cpp in audiofile (aka libaudiofile and Audio File Library) 0.3.6 allows remote attackers to have unspecified impact via a crafted audio file. 2017-03-15 audiofile -- audiofile Heap-based buffer overflow in the readValue function in FileHandle.cpp in audiofile (aka libaudiofile and Audio File Library) 0.3.6 allows remote attackers to have unspecified impact via a crafted WAV file.
2017-03-15 bigtreecms -- bigtree_cms CSRF exists in BigTree CMS 4.1.18 and 4.2.16 with the id parameter to the admin/ajax/users/delete/ page. A user can be deleted. 2017-03-15 bigtreecms -- bigtree_cms CSRF exists in BigTree CMS 4.1.18 with the colophon parameter to the admin/settings/update/ page. The Colophon can be changed. 2017-03-15 bigtreecms -- bigtree_cms CSRF exists in BigTree CMS 4.1.18 with the nav-social[#] parameter to the admin/settings/update/ page. The Navigation Social can be changed.
2017-03-15 bigtreecms -- bigtree_cms CSRF exists in BigTree CMS 4.2.16 with the value parameter to the admin/settings/update/ page. The Colophon can be changed. 2017-03-15 bigtreecms -- bigtree_cms CSRF exists in BigTree CMS 4.2.16 with the value[#][*] parameter to the admin/settings/update/ page. The Navigation Social can be changed. 2017-03-15 bitlbee -- bitlbee-libpurple BitlBee before 3.5 allows remote attackers to cause a denial of service (NULL pointer dereference and crash) and possibly execute arbitrary code via a file transfer request for a contact that is not in the contact list. 2017-03-14 cerberusftp -- ftp_server In Cerberus FTP Server 8.0.10.1, a crafted HTTP request causes the Windows service to crash. The attack methodology involves a long Host header and an invalid Content-Length header.
2017-03-14 debian -- debian_linux Stack-based buffer overflow in the evutil_parse_sockaddr_port function in evutil.c in libevent before 2.1.6-beta allows attackers to cause a denial of service (segmentation fault) via vectors involving a long string in brackets in the ip_as_string argument. 2017-03-15 debian -- debian_linux The search_make_new function in evdns.c in libevent before 2.1.6-beta allows attackers to cause a denial of service (out-of-bounds read) via an empty hostname. 2017-03-15 digisol -- dg-hr1400_router_firmware Privilege escalation vulnerability on the DIGISOL DG-HR1400 1.00.02 wireless router enables an attacker to escalate from user privilege to admin privilege just by modifying the Base64-encoded session cookie value. 2017-03-14 drupal -- drupal Some administrative paths in Drupal 8.2.x before 8.2.7 did not include protection for CSRF. This would allow an attacker to disable some blocks on a site.
This issue is mitigated by the fact that users would have to know the block ID. 2017-03-16 eaton -- xcomfort_ethernet_communication_interface An issue was discovered in Eaton xComfort Ethernet Communication Interface (ECI) Versions 1.07 and prior. By accessing a specific uniform resource locator (URL) on the webserver, a malicious user may be able to access files without authenticating.
2017-03-14 embedthis -- goahead A vulnerability in a custom-built GoAhead web server used on Foscam, Vstarcam, and multiple white-label IP camera models allows an attacker to craft a malformed HTTP ('GET system.ini HTTP/1.1 n n' - note the lack of '/' in the path field of the request) request that will disclose the configuration file with the login password. 2017-03-13 epson -- tmnet_webconfig Cross-site scripting (XSS) vulnerability in EPSON TMNet WebConfig 1.00 allows remote attackers to inject arbitrary web script or HTML via the W_AD1 parameter to Forms/oadmin_1. 2017-03-15 ettercap -- ettercap The compile_tree function in ef_compiler.c in the Etterfilter utility in Ettercap 0.8.2 and earlier allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted filter. 2017-03-15 evostream -- media_server A Buffer Overflow was discovered in EvoStream Media Server 1.7.1. A crafted HTTP request with a malicious header will cause a crash. An example attack methodology may include a long message-body in a GET request.
2017-03-10 fiyo -- fiyo_cms Fiyo CMS 2.0.6.1 allows remote authenticated users to gain privileges via a modified level parameter to dapur/ in an app=user&act=edit action. 2017-03-12 gnu -- glibc Integer overflow in the strxfrm function in the GNU C Library (aka glibc or libc6) before 2.21 allows context-dependent attackers to cause a denial of service (crash) or possibly execute arbitrary code via a long string, which triggers a stack-based buffer overflow. 2017-03-15 graphicsmagick -- graphicsmagick The QuantumTransferMode function in coders/tiff.c in GraphicsMagick 1.3.25 and earlier allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a small samples per pixel value in a CMYKA TIFF file. 2017-03-14 hikvision -- ds-76xxx_series_firmware Buffer overflow on Hikvision NVR DS-76xxNI-E1/2 and DS-77xxxNI-E4 devices before 3.4.0 allows remote authenticated users to cause a denial of service (service interruption) via a crafted HTTP request, aka the PSIA issue. 2017-03-13 hikvision -- ds-76xxx_series_firmware Buffer overflow on Hikvision NVR DS-76xxNI-E1/2 and DS-77xxxNI-E4 devices before 3.4.0 allows remote authenticated users to cause a denial of service (service interruption) via a crafted HTTP request, aka the ISAPI issue.
2017-03-13 hikvision -- ds-76xxx_series_firmware Buffer overflow on Hikvision NVR DS-76xxNI-E1/2 and DS-77xxxNI-E4 devices before 3.4.0 allows remote authenticated users to cause a denial of service (service interruption) via a crafted HTTP request, aka the SDK issue. 2017-03-13 imagemagick -- imagemagick Double free vulnerability in coders/tga.c in ImageMagick 7.0.0 and later allows remote attackers to cause a denial of service (application crash) via a crafted tga file.
2017-03-15 imagemagick -- imagemagick Integer overflow in coders/icon.c in ImageMagick 6.9.1-3 and later allows remote attackers to cause a denial of service (application crash) via a crafted length value, which triggers a buffer overflow. 2017-03-15 imagemagick -- imagemagick Integer truncation issue in coders/pict.c in ImageMagick before 7.0.5-0 allows remote attackers to cause a denial of service (application crash) via a crafted.pict file. 2017-03-15 imagemagick -- imagemagick The SpliceImage function in MagickCore/transform.c in ImageMagick before 6.9.2-4 allows remote attackers to cause a denial of service (application crash) via a crafted png file.
2017-03-15 imagemagick -- imagemagick The WriteImages function in magick/constitute.c in ImageMagick before 6.9.2-4 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted image file. 2017-03-15 intel_security_mcafee -- endpoint_security_web_control Cross-site scripting vulnerability in Intel Security McAfee Endpoint Security (ENS) Web Control before 10.2.0.408.10 allows attackers to inject arbitrary web script or HTML via a crafted web site. 2017-03-14 jasper_project -- jasper The jpc_tsfb_synthesize function in jpc_tsfb.c in JasPer before 1.900.9 allows remote attackers to cause a denial of service (NULL pointer dereference) via vectors involving an empty sequence.
2017-03-15 jasper_project -- jasper Integer overflow in the jpc_dec_tiledecode function in jpc_dec.c in JasPer before 1.900.12 allows remote attackers to have unspecified impact via a crafted image file, which triggers a heap-based buffer overflow. 2017-03-15 jasper_project -- jasper The jp2_colr_destroy function in jp2_cod.c in JasPer before 1.900.13 allows remote attackers to cause a denial of service (NULL pointer dereference) by leveraging incorrect cleanup of JP2 box data on error. NOTE: this vulnerability exists because of an incomplete fix for CVE-2016-8887. 2017-03-15 jasper_project -- jasper Integer overflow in the jpc_pi_nextcprl function in jpc_t2cod.c in JasPer before 1.900.20 allows remote attackers to have unspecified impact via a crafted file, which triggers use of an uninitialized value. 2017-03-15 jasper_project -- jasper The jas_matrix_asl function in jas_seq.c in JasPer 1.900.27 allows remote attackers to cause a denial of service (invalid memory read and crash) via a crafted image. 2017-03-16 jasper_project -- jasper The jp2_cdef_destroy function in jp2_cod.c in JasPer before 2.0.13 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted image.
2017-03-15 jasper_project -- jasper The jas_matrix_bindsub function in jas_seq.c in JasPer 2.0.10 allows remote attackers to cause a denial of service (invalid read) via a crafted image. 2017-03-15 jasper_project -- jasper Heap-based buffer overflow in the jpc_dec_decodepkt function in jpc_t2dec.c in JasPer 2.0.10 allows remote attackers to have unspecified impact via a crafted image. 2017-03-15 jquery -- jquery-ui Cross-site scripting (XSS) vulnerability in jQuery UI before 1.12.0 might allow remote attackers to inject arbitrary web script or HTML via the closeText parameter of the dialog function. 2017-03-15 keekoonvision -- kk002_ip_camera_firmware Keekoon KK002 devices 1.8.12 HD have a Cross Site Request Forgery Vulnerability affecting goform/formChnUserPwd and goform/formUserMng (and the entire set of other pages). 2017-03-13 lg_project -- lg Cross-site scripting (XSS) vulnerability in lg.cgi in Cougar LG 1.9 allows remote attackers to inject arbitrary web script or HTML via the 'addr' parameter. 2017-03-13 libgd -- libgd The gdImageCreateFromGd2Ctx function in gd_gd2.c in the GD Graphics Library (aka libgd) before 2.2.4 allows remote attackers to cause a denial of service (application crash) via a crafted image file.
2017-03-15 libgd -- libgd Integer overflow in gd_io.c in the GD Graphics Library (aka libgd) before 2.2.4 allows remote attackers to have unspecified impact via vectors involving the number of horizontal and vertical chunks in an image. 2017-03-15 libgd -- libgd The read_image_tga function in gd_tga.c in the GD Graphics Library (aka libgd) before 2.2.4 allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted TGA file, related to the decompression buffer. 2017-03-15 libplist_project -- libplist Heap-based buffer overflow in the parse_unicode_node function in bplist.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (out-of-bounds write) and possibly code execution via a crafted plist file. 2017-03-15 linux -- linux_kernel Race condition in kernel/ucount.c in the Linux kernel through 4.10.2 allows local users to cause a denial of service (use-after-free and system crash) or possibly have unspecified other impact via crafted system calls that leverage certain decrement behavior that causes incorrect interaction between put_ucounts and get_ucounts.
2017-03-14 lutim_project -- lutim Cross-site scripting (XSS) vulnerability in SVG file handling in Lutim 0.7.1 and earlier allows remote attackers to inject arbitrary web script. 2017-03-14 mangoswebv4_project -- mangoswebv4 paintballrefjosh/MaNGOSWebV4 4.0.8 is vulnerable to a reflected XSS in inc/admin/template_files/admin.faq.php (id parameter). 2017-03-11 mangoswebv4_project -- mangoswebv4 paintballrefjosh/MaNGOSWebV4 4.0.8 is vulnerable to a reflected XSS in inc/admin/template_files/admin.donate.php (id parameter). 2017-03-11 mangoswebv4_project -- mangoswebv4 paintballrefjosh/MaNGOSWebV4 4.0.8 is vulnerable to a reflected XSS in inc/admin/template_files/admin.fplinks.php (linkid parameter). 2017-03-11 mangoswebv4_project -- mangoswebv4 paintballrefjosh/MaNGOSWebV4 4.0.8 is vulnerable to a reflected XSS in inc/admin/template_files/admin.shop.php (id parameter). 2017-03-11 mangoswebv4_project -- mangoswebv4 paintballrefjosh/MaNGOSWebV4 4.0.8 is vulnerable to a reflected XSS in inc/admin/template_files/admin.vote.php (id parameter). 2017-03-11 mantisbt -- mantisbt A cross-site scripting (XSS) vulnerability in view_filters_page.php in MantisBT before 2.2.1 allows remote attackers to inject arbitrary JavaScript via the 'view_type' parameter.
2017-03-10 mcafee -- virusscan_enterprise Special element injection vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows authenticated remote attackers to read files on the webserver via a crafted user input. 2017-03-14 mcafee -- virusscan_enterprise Cross-site request forgery (CSRF) vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows authenticated remote attackers to execute unauthorized commands via a crafted user input. 2017-03-14 mcafee -- virusscan_enterprise Cross-site scripting (XSS) vulnerability in attributes in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows unauthenticated remote attackers to inject arbitrary web script or HTML via a crafted user input. 2017-03-14 mcafee -- virusscan_enterprise Improper control of generation of code vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote authenticated users to execute arbitrary code via a crafted HTTP request parameter. 2017-03-14 mcafee -- virusscan_enterprise Authentication bypass by spoofing vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote unauthenticated attacker to execute arbitrary code or cause a denial of service via a crafted authentication cookie.
2017-03-14 mcafee -- virusscan_enterprise Authentication bypass by assumed-immutable data vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote unauthenticated attacker to bypass server authentication via a crafted authentication cookie. 2017-03-14 mcafee -- virusscan_enterprise Improper neutralization of CRLF sequences in HTTP headers vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote unauthenticated attacker to obtain sensitive information via the server HTTP response spoofing. 2017-03-14 mcafee -- virusscan_enterprise SQL injection vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote authenticated users to obtain product information via a crafted HTTP request parameter.
2017-03-14 microsoft -- edge Microsoft Edge allows remote attackers to obtain sensitive information via a crafted web site, aka 'Microsoft Edge Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0009, CVE-2017-0017, CVE-2017-0065, and CVE-2017-0068. 2017-03-16 microsoft -- edge Microsoft Internet Explorer 11 and Microsoft Edge allow remote attackers to spoof web content via a crafted web site, aka 'Microsoft Browser Spoofing Vulnerability.' This vulnerability is different from those described in CVE-2017-0033 and CVE-2017-0069.
2017-03-16 microsoft -- edge The RegEx class in the XSS filter in Microsoft Edge allows remote attackers to conduct cross-site scripting (XSS) attacks and obtain sensitive information via unspecified vectors, aka 'Microsoft Edge Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0009, CVE-2017-0011, CVE-2017-0065, and CVE-2017-0068. 2017-03-16 microsoft -- edge Microsoft Internet Explorer 11 and Microsoft Edge allow remote attackers to spoof web content via a crafted web site, aka 'Microsoft Browser Spoofing Vulnerability.' This vulnerability is different from those described in CVE-2017-0012 and CVE-2017-0069. 2017-03-16 microsoft -- edge Microsoft Edge allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Microsoft Browser Information Disclosure Vulnerability.'
This vulnerability is different from those described in CVE-2017-0009, CVE-2017-0011, CVE-2017-0017, and CVE-2017-0068. 2017-03-16 microsoft -- edge Browsers in Microsoft Edge allow remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Microsoft Edge Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0009, CVE-2017-0011, CVE-2017-0017, and CVE-2017-0065.
2017-03-16 microsoft -- edge Microsoft Edge allows remote attackers to spoof web content via a crafted web site, aka 'Microsoft Edge Spoofing Vulnerability.' This vulnerability is different from those described in CVE-2017-0012 and CVE-2017-0033. 2017-03-16 microsoft -- edge Microsoft Edge allows remote attackers to bypass the Same Origin Policy for HTML elements in other browser windows, aka 'Microsoft Edge Security Feature Bypass Vulnerability.' This vulnerability is different from those described in CVE-2017-0066 and CVE-2017-0140. 2017-03-16 microsoft -- edge Microsoft Edge allows remote attackers to bypass the Same Origin Policy for HTML elements in other browser windows, aka 'Microsoft Edge Security Feature Bypass Vulnerability.' This vulnerability is different from those described in CVE-2017-0066 and CVE-2017-0135.
2017-03-16 microsoft -- internet_explorer Microsoft Internet Explorer 9 through 11 allow remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Internet Explorer Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0009 and CVE-2017-0059. 2017-03-16 microsoft -- internet_explorer Microsoft Internet Explorer 9 through 11 allow remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Microsoft Browser Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0011, CVE-2017-0017, CVE-2017-0065, and CVE-2017-0068.
2017-03-16 microsoft -- internet_explorer The VBScript engine in Microsoft Internet Explorer 11 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Scripting Engine Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0018, and CVE-2017-0037. 2017-03-16 microsoft -- internet_explorer Microsoft Internet Explorer 9 through 11 allow remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Internet Explorer Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0008 and CVE-2017-0009. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Uniscribe Remote Code Execution Vulnerability.'
This vulnerability is different from those described in CVE-2017-0083, CVE-2017-0084, CVE-2017-0086, CVE-2017-0087, CVE-2017-0088, CVE-2017-0089, and CVE-2017-0090. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128.
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.'
CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128.
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Windows Uniscribe Information Disclosure Vulnerability.'
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128.
2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, and CVE-2017-0128. 2017-03-16 microsoft -- windows_vista Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, and Windows 7 SP1 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.'
CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, and CVE-2017-0127. 2017-03-16 netpbm -- netpbm tiffttopnm in netpbm 10.47.63 does not properly use the libtiff TIFFRGBAImageGet function, which allows remote attackers to cause a denial of service (out-of-bounds read and write) via a crafted tiff image file, related to transposing width and height values. 2017-03-15 open_edx -- edx-platform Open edX edx-platform before 2015-08-25 requires use of the database for storage of SAML SSO secrets, which makes it easier for context-dependent attackers to obtain sensitive information by leveraging access to a database backup. 2017-03-13 paloaltonetworks -- pan-os The Management Web Interface in Palo Alto Networks PAN-OS before 6.1.16, 7.0.x before 7.0.13, and 7.1.x before 7.1.8 allows remote authenticated users to read arbitrary files via unspecified vectors. 2017-03-15 partclone_project -- partclone partclone.chkimg in partclone 0.2.89 is prone to a heap-based buffer overflow vulnerability due to insufficient validation of the partclone image header. An attacker may be able to launch a 'Denial of Service attack' in the context of the user running the affected application.
2017-03-10 pharos -- popup A denial of service vulnerability exists in the psnotifyd application of the Pharos PopUp printer client version 9.0. A specially crafted packet can be sent to the victim's computer and can lead to an out of bounds read causing a crash and a denial of service. 2017-03-10 podofo_project -- podofo The ColorChanger::GetColorFromStack function in colorchanger.cpp in PoDoFo 0.9.5 allows remote attackers to cause a denial of service (invalid read) via a crafted file. 2017-03-15 podofo_project -- podofo The GraphicsStack::TGraphicsStackElement::~TGraphicsStackElement function in graphicsstack.h in PoDoFo 0.9.5 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 podofo_project -- podofo The ColorChanger::GetColorFromStack function in colorchanger.cpp in PoDoFo 0.9.5 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 podofo_project -- podofo Heap-based buffer overflow in the PoDoFo::PdfVariant::DelayedLoad function in PdfVariant.h in PoDoFo 0.9.4 allows remote attackers to have unspecified impact via a crafted file.
2017-03-15 podofo_project -- podofo Buffer overflow in the PoDoFo::PdfParser::ReadXRefSubsection function in PdfParser.cpp in PoDoFo 0.9.4 allows remote attackers to have unspecified impact via a crafted file. 2017-03-15 podofo_project -- podofo The PoDoFo::PdfColor::operator function in PdfColor.cpp in PoDoFo 0.9.4 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 podofo_project -- podofo The GraphicsStack::TGraphicsStackElement::SetNonStrokingColorSpace function in graphicsstack.h in PoDoFo 0.9.4 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 podofo_project -- podofo The PoDoFo::PdfVariant::DelayedLoad function in PdfVariant.h in PoDoFo 0.9.4 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 podofo_project -- podofo The PoDoFo::PdfXObject::PdfXObject function in PdfXObject.cpp in PoDoFo 0.9.5 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file.
2017-03-15 podofo_project -- podofo The PoDoFo::PdfColorGray::~PdfColorGray function in PdfColor.cpp in PoDoFo 0.9.4 allows remote attackers to cause a denial of service (NULL pointer dereference) via a crafted file. 2017-03-15 qemu -- qemu Memory leak in hw/watchdog/wdt_i6300esb.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (host memory consumption and QEMU process crash) via a large number of device unplug operations. 2017-03-15 qemu -- qemu Memory leak in hw/audio/ac97.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (host memory consumption and QEMU process crash) via a large number of device unplug operations. 2017-03-15 qemu -- qemu Memory leak in hw/audio/es1370.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (host memory consumption and QEMU process crash) via a large number of device unplug operations.
2017-03-15 qemu -- qemu Memory leak in the virgl_resource_attach_backing function in hw/display/virtio-gpu-3d.c in QEMU (aka Quick Emulator) allows local guest OS users to cause a denial of service (host memory consumption) via a large number of VIRTIO_GPU_CMD_RESOURCE_ATTACH_BACKING commands. 2017-03-15 qemu -- qemu Memory leak in the virtio_gpu_resource_attach_backing function in hw/display/virtio-gpu.c in QEMU (aka Quick Emulator) allows local guest OS users to cause a denial of service (host memory consumption) via a large number of VIRTIO_GPU_CMD_RESOURCE_ATTACH_BACKING commands. 2017-03-15 qemu -- qemu Memory leak in the serial_exit_core function in hw/char/serial.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (host memory consumption and QEMU process crash) via a large number of device unplug operations.
2017-03-15 qemu -- qemu Memory leak in the megasas_handle_dcmd function in hw/scsi/megasas.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (host memory consumption) via MegaRAID Firmware Interface (MFI) commands with the sglist size set to a value over 2 Gb. 2017-03-16 qemu -- qemu Memory leak in the virgl_cmd_resource_unref function in hw/display/virtio-gpu-3d.c in QEMU (aka Quick Emulator) allows local guest OS users to cause a denial of service (host memory consumption) via a large number of VIRTIO_GPU_CMD_RESOURCE_UNREF commands sent without detaching the backing storage beforehand. 2017-03-16 r_project -- r An exploitable buffer overflow vulnerability exists in the LoadEncoding functionality of the R programming language version 3.3.0. A specially crafted R script can cause a buffer overflow resulting in a memory corruption. An attacker can send a malicious R script to trigger this vulnerability. 2017-03-10 roundcube -- roundcube_webmail rcube_utils.php in Roundcube before 1.1.8 and 1.2.x before 1.2.4 is susceptible to a cross-site scripting vulnerability via a crafted Cascading Style Sheets (CSS) token sequence within an SVG element.
2017-03-12 sap -- businessobjects_financial_consolidation Cross-site scripting (XSS) vulnerability in the help component of SAP BusinessObjects Financial Consolidation 10.0.0.1933 allows remote attackers to inject arbitrary web script or HTML via a GET request. /finance/help/en/frameset.htm is the URI for this component. The vendor response is SAP Security Note 2368106. 2017-03-16 softaculous -- whmcs_reseller_module The WHMCS Reseller Module V2 2.0.2 in Softaculous Virtualizor before 2.9.1.0 does not verify the user correctly, which allows remote authenticated users to control other virtual machines managed by Virtualizor by accessing a modified URL. 2017-03-11 telegram -- messenger An issue was discovered in Telegram Messenger 2.6 for iOS and 1.8.2 for Android.
Secret chat messages are available in cleartext in process memory and a.db file. 2017-03-14 uninett -- mod_auth_mellon mod_auth_mellon before 0.13.1 is vulnerable to a Cross-Site Session Transfer attack, where a user with access to one web site running on a server can copy their session cookie to a different web site on the same server to get access to that site. 2017-03-13 viewvc -- viewvc Cross-site scripting (XSS) vulnerability in the nav_path function in lib/viewvc.py in ViewVC before 1.1.26 allows remote attackers to inject arbitrary web script or HTML via the nav_data name. 2017-03-15 virglrenderer_project -- virglrenderer Memory leak in the vrend_renderer_context_create_internal function in vrend_decode.c in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (host memory consumption) by repeatedly creating a decode context. 2017-03-15 virglrenderer_project -- virglrenderer Memory leak in the vrend_renderer_init_blit_ctx function in vrend_blitter.c in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (host memory consumption) via a large number of VIRGL_CCMD_BLIT commands.
2017-03-15 virglrenderer_project -- virglrenderer Memory leak in the add_shader_program function in vrend_renderer.c in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (host memory consumption) via vectors involving the sprog variable. 2017-03-15 virglrenderer_project -- virglrenderer Memory leak in the vrend_create_vertex_elements_state function in vrend_renderer.c in virglrenderer allows local guest OS users to cause a denial of service (host memory consumption) via a large number of VIRGL_OBJECT_VERTEX_ELEMENTS commands.
2017-03-15 wavpack_project -- wavpack The read_code function in read_words.c in Wavpack before 5.1.0 allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted WV file. 2017-03-14 wavpack_project -- wavpack The WriteCaffHeader function in cli/caff.c in Wavpack before 5.1.0 allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted WV file. 2017-03-14 wavpack_project -- wavpack The unreorder_channels function in cli/wvunpack.c in Wavpack before 5.1.0 allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted WV file. 2017-03-14 wavpack_project -- wavpack The read_new_config_info function in open_utils.c in Wavpack before 5.1.0 allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted WV file. 2017-03-14 wordpress -- wordpress In WordPress before 4.7.3 (wp-includes/pluggable.php), control characters can trick redirect URL validation.
2017-03-11 wordpress -- wordpress In WordPress before 4.7.3 (wp-admin/plugins.php), unintended files can be deleted by administrators using the plugin deletion functionality. 2017-03-11 wordpress -- wordpress In WordPress before 4.7.3 (wp-admin/js/tags-box.js), there is cross-site scripting (XSS) via taxonomy term names.
2017-03-11 wordpress -- wordpress In WordPress before 4.7.3, there is cross-site request forgery (CSRF) in Press This (wp-admin/includes/class-wp-press-this.php), leading to excessive use of server resources. The CSRF can trigger an outbound HTTP request for a large file that is then parsed by Press This. 2017-03-11 ytnef_project -- ytnef An issue was discovered in ytnef before 1.9.2. An invalid memory access (heap-based buffer over-read) can occur during handling of LONG data types, related to MAPIPrint() in libytnef. 2017-03-10 ytnef_project -- ytnef An issue was discovered in ytnef before 1.9.2.
There is a potential out-of-bounds access with fields of Size 0 in TNEFParse() in libytnef. 2017-03-10 ytnef_project -- ytnef An issue was discovered in ytnef before 1.9.2. There is a potential heap-based buffer over-read on incoming Compressed RTF Streams, related to DecompressRTF() in libytnef. 2017-03-10 zahmit_design -- connections_business_directory_plugin Cross-site scripting (XSS) vulnerability in includes/admin/pages/manage.php in the Connections Business Directory plugin before 8.5.9 for WordPress allows remote attackers to inject arbitrary web script or HTML via the s variable.
2017-03-16 zammad -- zammad An XSS issue was discovered in Zammad before 1.0.4, 1.1.x before 1.1.3, and 1.2.x before 1.2.1. Attachments are opened in a new tab instead of getting downloaded. This creates an attack vector of executing code in the domain of the application. 2017-03-13 zammad -- zammad An issue was discovered in Zammad before 1.0.4, 1.1.x before 1.1.3, and 1.2.x before 1.2.1. XSS can be triggered via malicious HTML in a chat message or the content of a ticket article, when using either the REST API or the WebSocket API. 2017-03-13 zammad -- zammad A CSRF issue was discovered in Zammad before 1.0.4, 1.1.x before 1.1.3, and 1.2.x before 1.2.1.
To exploit the vulnerability, an attacker can send cross-domain requests directly to the REST API for users with a valid session cookie. Low Vulnerabilities Primary Vendor -- Product Description Published CVSS Score Source & Patch Info busybox -- busybox The add_probe function in modutils/modprobe.c in BusyBox before 1.23.0 allows local users to bypass intended restrictions on loading kernel modules via a / (slash) character in a module name, as demonstrated by an 'ifconfig /usbserial up' command or a 'mount -t /snd_pcm none /' command. 2017-03-12 foxitsoftware -- phantompdf The ConvertToPDF plugin in Foxit Reader before 8.2.1 and PhantomPDF before 8.2.1 on Windows, when the gflags app is enabled, allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted TIFF image. The vulnerability could lead to information disclosure; an attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the current process. 2017-03-14 libplist_project -- libplist The parse_string_node function in bplist.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (memory corruption) via a crafted plist file. 2017-03-15 libplist_project -- libplist The parse_string_node function in bplist.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (memory allocation error) via a crafted plist file. 2017-03-15 libplist_project -- libplist The base64encode function in base64.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (out-of-bounds read) via a crafted plist file.
2017-03-15 libplist_project -- libplist Heap-based buffer overflow in the parse_string_node function in bplist.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (out-of-bounds write) via a crafted plist file. 2017-03-15 libplist_project -- libplist The parse_data_node function in bplist.c in libimobiledevice libplist 1.12 allows local users to cause a denial of service (memory allocation error) via a crafted plist file. 2017-03-15 mcafee -- application_control A write protection and execution bypass vulnerability in McAfee (now Intel Security) Application Control (MAC) 6.1.0 for Linux and earlier allows authenticated users to change binaries that are part of the Application Control whitelist and allows execution of binaries via specific conditions.
2017-03-14 mcafee -- application_control A write protection and execution bypass vulnerability in McAfee (now Intel Security) Change Control (MCC) 6.1.0 for Linux and earlier allows authenticated users to change files that are part of write protection rules via specific conditions. 2017-03-14 mcafee -- virusscan_enterprise Information exposure in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows authenticated remote attackers to obtain the existence of unauthorized files on the system via a URL parameter. 2017-03-14 mcafee -- virusscan_enterprise Improper verification of cryptographic signature vulnerability in Intel Security VirusScan Enterprise Linux (VSEL) 2.0.3 (and earlier) allows remote authenticated users to spoof update server and execute arbitrary code via a crafted input file. 2017-03-14 microsoft -- windows_10 Microsoft Windows 10 1607 and Windows Server 2016 allow remote attackers to cause a denial of service (application hang) via a crafted Office document, aka 'Microsoft Hyper-V Network Switch Denial of Service Vulnerability.' This vulnerability is different from those described in CVE-2017-0074, CVE-2017-0076, CVE-2017-0097, CVE-2017-0098, and CVE-2017-0099.
2017-03-16 paloaltonetworks -- pan-os Cross-site scripting (XSS) vulnerability in the Management Web Interface in Palo Alto Networks PAN-OS 5.1, 6.x before 6.1.16, 7.0.x before 7.0.13, and 7.1.x before 7.1.8 allows remote authenticated users to inject arbitrary web script or HTML via unspecified vectors. 2017-03-15 qemu -- qemu The sdhci_sdma_transfer_multi_blocks function in hw/sd/sdhci.c in QEMU (aka Quick Emulator) allows local guest OS privileged users to cause a denial of service (out-of-bounds heap access and crash) or execute arbitrary code on the QEMU host via vectors involving the data transfer length. 2017-03-16 qemu -- qemu The ohci_service_ed_list function in hw/usb/hcd-ohci.c in QEMU (aka Quick Emulator) allows local guest OS users to cause a denial of service (infinite loop) via vectors involving the number of link endpoint list descriptors. 2017-03-15 suse -- linux_enterprise_server Integer overflow in the emulated_apdu_from_guest function in usb/dev-smartcard-reader.c in Quick Emulator (Qemu), when built with the CCID Card device emulator support, allows local users to cause a denial of service (application crash) via a large Application Protocol Data Units (APDU) unit. 2017-03-15 virglrenderer_project -- virglrenderer The parse_instruction function in gallium/auxiliary/tgsi/tgsi_text.c in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (out-of-bounds array access and process crash) via a crafted texture instruction. 2017-03-15 virglrenderer_project -- virglrenderer The util_format_is_pure_uint function in vrend_renderer.c in Virgil 3d project (aka virglrenderer) 0.6.0 and earlier allows local guest OS users to cause a denial of service (NULL pointer dereference) via a crafted VIRGL_CCMD_CLEAR command. 2017-03-15 virglrenderer_project -- virglrenderer Stack-based buffer overflow in the vrend_decode_set_framebuffer_state function in vrend_decode.c in virglrenderer before 926b9b34d8bbe9e4437f, as used in Quick Emulator (QEMU), allows a local guest users to cause a denial of service (application crash) via the 'nr_cbufs' argument.
2017-03-14 virglrenderer_project -- virglrenderer Heap-based buffer overflow in the vrend_create_vertex_elements_state function in vrend_renderer.c in virglrenderer before 0.6. Elektra Beckum Bandsaw Bas 315 Manual Treadmill. 0 allows local guest OS users to cause a denial of service (out-of-bounds array access and crash) via the num_elements parameter. 2017-03-15 virglrenderer_project -- virglrenderer Stack-based buffer overflow in the parse_identifier function in tgsi_text.c in the TGSI auxiliary module in the Gallium driver in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (out-of-bounds array access and QEMU process crash) via vectors related to parsing properties.
2017-03-15 virglrenderer_project -- virglrenderer The vrend_decode_reset function in vrend_decode.c in virglrenderer before 0.6.0 allows local guest OS users to cause a denial of service (NULL pointer dereference and QEMU process crash) by destroying context 0 (zero). 2017-03-15 wordpress -- wordpress In WordPress before 4.7.3, there is authenticated Cross-Site Scripting (XSS) via Media File Metadata. This is demonstrated by both (1) mishandling of the playlist shortcode in the wp_playlist_shortcode function in wp-includes/media.php and (2) mishandling of meta information in the renderTracks function in wp-includes/js/mediaelement/wp-playlist.js. 2017-03-11 wordpress -- wordpress In WordPress before 4.7.3 (wp-includes/embed.php), there is authenticated Cross-Site Scripting (XSS) in YouTube URL Embeds. Severity Not Yet Assigned Primary Vendor -- Product Description Published CVSS Score Source & Patch Info amazon -- kindle Untrusted search path vulnerability in Amazon Kindle for PC before 1.19 allows local users to execute arbitrary code and conduct DLL hijacking attacks via a Trojan horse DLL in the current working directory of the Kindle Setup installer. 2017-03-15 not yet calculated apache -- camel Apache Camel's Validation Component is vulnerable against SSRF via remote DTDs and XXE. 2017-03-16 not yet calculated apng2gif -- apng2gif An issue was discovered in apng2gif 1.7.
There is improper sanitization of user input causing huge memory allocations, resulting in a crash. This is related to the read_chunk function using the pChunk->size value (within the PNG file) to determine the amount of memory to allocate. 2017-03-17 not yet calculated apng2gif -- apng2gif An issue was discovered in apng2gif 1.7. There is an integer overflow resulting in a heap-based buffer over-read, related to the load_apng function and the imagesize variable. 2017-03-17 not yet calculated apng2gif -- apng2gif An issue was discovered in apng2gif 1.7.
There is an integer overflow resulting in a heap-based buffer overflow. This is related to the read_chunk function making an unchecked addition of 12. 2017-03-17 not yet calculated aura -- easycom Stack-based buffer overflows in php_Easycom5_3_0.dll in EasyCom for PHP 4.0.0.29 allows remote attackers to execute arbitrary code via the server argument to the (1) i5_connect, (2) i5_pconnect, or (3) i5_private_connect API function. 2017-03-15 not yet calculated aura -- easycom EasyCom SQL iPlug allows remote attackers to cause a denial of service via the D$EVAL parameter to the default URI. 2017-03-15 not yet calculated calibre -- e-book_viewer The E-book viewer in calibre before 2.75 allows remote attackers to read arbitrary files via a crafted epub file with JavaScript. 2017-03-16 not yet calculated capstone -- capstone Integer overflow in the cs_winkernel_malloc function in winkernel_mm.c in Capstone 3.0.4 and earlier allows attackers to cause a denial of service (heap-based buffer overflow in a kernel driver) or possibly have unspecified other impact via a large value. 2017-03-16 not yet calculated cerberus -- cerberus Buffer overflow in Cerberus FTP Server 8.0.10.3 allows remote attackers to cause a denial of service (daemon crash) or possibly have unspecified other impact via a long MLST command.
2017-03-17 not yet calculated chef_manage -- chef_manage The user-account creation feature in Chef Manage 2.1.0 through 2.4.4 allows remote attackers to execute arbitrary code. This is fixed in 2.4.5. 2017-03-17 not yet calculated chicken -- chicken An issue was discovered in CHICKEN Scheme through 4.12.0. When using a nonstandard CHICKEN-specific extension to allocate an SRFI-4 vector in unmanaged memory, the vector size would be used in unsanitised form as an argument to malloc(). With an unexpected size, the impact may have been a segfault or buffer overflow. 2017-03-16 not yet calculated cisco -- adaptive_security_appliance A vulnerability in the Border Gateway Protocol (BGP) Bidirectional Forwarding Detection (BFD) implementation of Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to bypass the access control list (ACL) for specific TCP and UDP traffic. More Information: CSCvc68229.
Known Affected Releases: 9.6(2). Known Fixed Releases: 99.1(20.1) 99.1(10.2) 98.1(12.7) 98.1(1.49) 97.1(6.58) 97.1(0.134) 96.2(0.109) 9.7(1.1) 9.6(2.99) 9.6(2.8). 2017-03-17 not yet calculated cisco -- wireless_lan_controller A vulnerability in the mesh code of Cisco Wireless LAN Controller (WLC) software could allow an unauthenticated, remote attacker to impersonate a WLC in a meshed topology. The vulnerability is due to insufficient authentication of the parent access point in a mesh configuration. An attacker could exploit this vulnerability by forcing the target system to disconnect from the correct parent access point and reconnect to a rogue access point owned by the attacker. An exploit could allow the attacker to control the traffic flowing through the impacted access point or take full control of the target system. This vulnerability affects the following products running a vulnerable version of Wireless LAN Controller software and configured for meshed mode: Cisco 8500 Series Wireless Controller, Cisco 5500 Series Wireless Controller, Cisco 2500 Series Wireless Controller, Cisco Flex 7500 Series Wireless Controller, Cisco Virtual Wireless Controller, Wireless Services Module 2 (WiSM2).
Note that additional configuration is needed in addition to upgrading to a fixed release. Cisco Bug IDs: CSCuc98992 CSCuu14804. 2017-03-15 not yet calculated cisco -- client_manager_server A vulnerability in the Client Manager Server of Cisco Workload Automation and Cisco Tidal Enterprise Scheduler could allow an unauthenticated, remote attacker to retrieve any file from the Client Manager Server. The vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by sending a crafted URL to the Client Manager Server. An exploit could allow the attacker to retrieve any file from the Cisco Workload Automation or Cisco Tidal Enterprise Scheduler Client Manager Server.
This vulnerability affects the following products: Cisco Tidal Enterprise Scheduler Client Manager Server releases 6.2.1.435 and later, Cisco Workload Automation Client Manager Server releases 6.3.0.116 and later. Cisco Bug IDs: CSCvc90789. 2017-03-15 not yet calculated cisco -- cluster_management_protocol A vulnerability in the Cisco Cluster Management Protocol (CMP) processing code in Cisco IOS and Cisco IOS XE Software could allow an unauthenticated, remote attacker to cause a reload of an affected device or remotely execute code with elevated privileges.
The Cluster Management Protocol utilizes Telnet internally as a signaling and command protocol between cluster members. The vulnerability is due to the combination of two factors: (1) the failure to restrict the use of CMP-specific Telnet options only to internal, local communications between cluster members and instead accept and process such options over any Telnet connection to an affected device; and (2) the incorrect processing of malformed CMP-specific Telnet options. An attacker could exploit this vulnerability by sending malformed CMP-specific Telnet options while establishing a Telnet session with an affected Cisco device configured to accept Telnet connections. An exploit could allow an attacker to execute arbitrary code and obtain full control of the device or cause a reload of the affected device. This affects Catalyst switches, Embedded Service 2020 switches, Enhanced Layer 2 EtherSwitch Service Module, Enhanced Layer 2/3 EtherSwitch Service Module, Gigabit Ethernet Switch Module (CGESM) for HP, IE Industrial Ethernet switches, ME 4924-10GE switch, RF Gateway 10, and SM-X Layer 2/3 EtherSwitch Service Module. Cisco Bug IDs: CSCvd48893.
2017-03-17 not yet calculated cisco -- mobility_express A vulnerability in the web-based GUI of Cisco Mobility Express 1800 Series Access Points could allow an unauthenticated, remote attacker to bypass authentication. The attacker could be granted full administrator privileges. The vulnerability is due to improper implementation of authentication for accessing certain web pages using the GUI interface. An attacker could exploit this vulnerability by sending a crafted HTTP request to the web interface of the affected system. A successful exploit could allow the attacker to bypass authentication and perform unauthorized configuration changes or issue control commands to the affected device.
This vulnerability affects Cisco Mobility Express 1800 Series Access Points running a software version prior to 8.2.110.0. Cisco Bug IDs: CSCuy68219. 2017-03-15 not yet calculated cisco -- nexus_7000_series_switches An Access-Control Filtering Mechanisms Bypass vulnerability in certain access-control filtering mechanisms on Cisco Nexus 7000 Series Switches could allow an unauthenticated, remote attacker to bypass defined traffic configured within an access control list (ACL) on the affected system. More Information: CSCtz59354. Known Affected Releases: 5.2(4) 6.1(3)S5 6.1(3)S6 6.2(1.121)S0 7.2(1)D1(1) 7.3(0)ZN(0.161) 7.3(1)N1(0.1). Known Fixed Releases: 7.3(0)D1(1) 6.2(2) 6.1(5) 8.3(0)KMT(0.24) 8.3(0)CV(0.337) 7.3(1)N1(1) 7.3(0)ZN(0.210) 7.3(0)ZN(0.177) 7.3(0)ZD(0.194) 7.3(0)TSH(0.99) 7.3(0)SC(0.14) 7.3(0)RSP(0.7) 7.3(0)N1(1) 7.3(0)N1(0.193) 7.3(0)IZN(0.13) 7.3(0)IB(0.102) 7.3(0)GLF(0.44) 7.3(0)D1(0.178) 7.1(0)D1(0.14) 7.0(3)ITI2(1.6) 7.0(3)ISH1(2.13) 7.0(3)IFD6(0.78) 7.0(3)IFD6(0) 7.0(3)IDE6(0.12) 7.0(3)IDE6(0) 7.0(3)I2(1) 7.0(3)I2(0.315) 7.0(1)ZD(0.3) 7.0(0)ZD(0.84) 6.2(1.149)S0 6.2(0.285) 6.1(5.32)S0 6.1(4.97)S0 6.1(2.30)S0. 2017-03-17 not yet calculated cisco -- nexus_9000_series_switches A Denial of Service vulnerability in the remote login functionality for Cisco NX-OS Software running on Cisco Nexus 9000 Series Switches could allow an unauthenticated, remote attacker to cause a process used for login to terminate unexpectedly and the login attempt to fail.
There is no impact to user traffic flowing through the device. The attacker could use either a Telnet or an SSH client for the remote login attempt. Affected Products: This vulnerability affects Cisco Nexus 9000 Series Switches that are running Cisco NX-OS Software and are configured to allow remote Telnet connections to the device. More Information: CSCuy25824. Known Affected Releases: 7.0(3)I3(1) 8.3(0)CV(0.342) 8.3(0)CV(0.345). Known Fixed Releases: 8.3(0)CV(0.362) 8.0(1) 7.0(3)IED5(0.19) 7.0(3)IED5(0) 7.0(3)I4(1) 7.0(3)I4(0.8) 7.0(3)I2(2e) 7.0(3)F1(1.22) 7.0(3)F1(1) 7.0(3)F1(0.230). 2017-03-17 not yet calculated cisco -- nexus_9000_series_switches A Denial of Service vulnerability in the Telnet remote login functionality of Cisco NX-OS Software running on Cisco Nexus 9000 Series Switches could allow an unauthenticated, remote attacker to cause a Telnet process used for login to terminate unexpectedly and the login attempt to fail.
There is no impact to user traffic flowing through the device. Affected Products: This vulnerability affects Cisco Nexus 9000 Series Switches that are running Cisco NX-OS Software and are configured to allow remote Telnet connections to the device. More Information: CSCux46778. Known Affected Releases: 7.0(3)I3(0.170). Known Fixed Releases: 7.0(3)I3(1) 7.0(3)I3(0.257) 7.0(3)I3(0.255) 7.0(3)I2(2e) 7.0(3)F1(1.22) 7.0(3)F1(1).
2017-03-17 not yet calculated cisco -- prime_infrastructure An API Credentials Management vulnerability in the APIs for Cisco Prime Infrastructure could allow an authenticated, remote attacker to access an API that should be restricted to a privileged user. The attacker needs to have valid credentials. More Information: CSCuy36192. Known Affected Releases: 3.1(1) 3.1(1). 2017-03-17 not yet calculated cisco -- prime_optical A RADIUS Secret Disclosure vulnerability in the web network management interface of Cisco Prime Optical for Service Providers could allow an authenticated, remote attacker to disclose sensitive information in the configuration generated for a device. The attacker must have valid credentials for the device. More Information: CSCvc65257.
Known Affected Releases: 10.6(0.1). 2017-03-17 not yet calculated cisco -- prime_service_catalog A vulnerability in the web framework code of Cisco Prime Service Catalog could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack against the user of the web interface of the affected system. More Information: CSCvc79842 CSCvc79846 CSCvc79855 CSCvc79873 CSCvc79882 CSCvc79891. Known Affected Releases: 11.1.2. 2017-03-17 not yet calculated cisco -- staros A privilege escalation vulnerability in the Secure Shell (SSH) subsystem in the StarOS operating system for Cisco ASR 5000 Series, ASR 5500 Series, ASR 5700 Series devices, and Cisco Virtualized Packet Core could allow an authenticated, remote attacker to gain unrestricted, root shell access. The vulnerability is due to missing input validation of parameters passed during SSH or SFTP login. An attacker could exploit this vulnerability by providing crafted user input to the SSH or SFTP command-line interface (CLI) during SSH or SFTP login.
An exploit could allow an authenticated attacker to gain root privileges access on the router. Note: Only traffic directed to the affected system can be used to exploit this vulnerability. This vulnerability can be triggered via both IPv4 and IPv6 traffic. An established TCP connection toward port 22, the SSH default port, is needed to perform the attack. The attacker must have valid credentials to login to the system via SSH or SFTP. The following products have been confirmed to be vulnerable: Cisco ASR 5000/5500/5700 Series devices running StarOS after 17.7.0 and prior to 18.7.4, 19.5, and 20.2.3 with SSH configured are vulnerable.
Cisco Virtualized Packet Core - Single Instance (VPC-SI) and Distributed Instance (VPC-DI) devices running StarOS prior to N4.2.7 (19.3.v7) and N4.7 (20.2.v0) with SSH configured are vulnerable. Cisco Bug IDs: CSCva65853. 2017-03-15 not yet calculated cisco -- telepresence An API Privilege vulnerability in Cisco TelePresence Server Software could allow an unauthenticated, remote attacker to emulate Cisco TelePresence Server endpoints.
Affected Products: This vulnerability affects Cisco TelePresence Server MSE 8710 Processors that are running a software release prior to Cisco TelePresence Software Release 4.3 and are running in locally managed mode. The vulnerable API was deprecated in Cisco TelePresence Software Release 4.3. More Information: CSCvc37616. 2017-03-17 not yet calculated cisco -- ucs_director A vulnerability in the web-based management interface of Cisco UCS Director could allow an unauthenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the web-based management interface of an affected device.
More Information: CSCvc44344. Known Affected Releases: 6.0(0.0). 2017-03-17 not yet calculated cisco -- unified_communications_manager A vulnerability in the web framework of Cisco Unified Communications Manager (CallManager) could allow an authenticated, remote attacker to perform a cross-site scripting (XSS) attack. More Information: CSCvb70033. Known Affected Releases: 11.5(1.11007.2). Known Fixed Releases: 12.0(0.98000.507) 11.0(1.23900.5) 11.0(1.23900.3) 10.5(2.15900.2).
2017-03-17 not yet calculated cisco -- unified_communications_manager A vulnerability in the web framework of Cisco Unified Communications Manager (CallManager) could allow an unauthenticated, remote attacker to conduct a cross-site request forgery (CSRF) attack against a user of the web interface of the affected software. More Information: CSCvb70021. Known Affected Releases: 11.5(1.11007.2).
2017-03-17 not yet calculated cisco -- unified_communications_manager A cross-site scripting (XSS) filter bypass vulnerability in the web-based management interface of Cisco Unified Communications Manager could allow an unauthenticated, remote attacker to conduct XSS attacks against a user of an affected device. More Information: CSCvc21620. Known Affected Releases: 10.5(2.14076.1). Known Fixed Releases: 12.0(0.98000.641) 12.0(0.98000.500) 12.0(0.98000.219).
2017-03-17 not yet calculated cisco -- web_security_appliance A vulnerability in the URL filtering feature of Cisco AsyncOS Software for Cisco Web Security Appliance (WSA) could allow an unauthenticated, remote attacker to bypass a configured URL filter rule. Affected Products: This vulnerability affects all releases prior to the first fixed release of Cisco AsyncOS Software for Cisco Web Security Appliance (WSA), both virtual and hardware appliances, that are configured with URL filters for email scanning. More Information: CSCvc69700. Known Affected Releases: 8.5.3-069 9.1.1-074 9.1.2-010. 2017-03-17 not yet calculated cisco -- webex An Authentication Bypass vulnerability in Cisco WebEx Meetings Server could allow an unauthenticated, remote attacker to access limited meeting information on the Cisco WebEx Meetings Server. More Information: CSCvd50728.
Known Affected Releases: 2.6 2.7 2.8 CWMS-2.5MR1 Orion1.1.2.patch T29_orion_merge. 2017-03-17 not yet calculated cisco -- webex An XML External Entity vulnerability in Cisco WebEx Meetings Server could allow an authenticated, remote attacker to have read access to part of the information stored in the affected system. More Information: CSCvc39165.
Known Affected Releases: 2.6. Known Fixed Releases: 2.7.1.2054. 2017-03-17 not yet calculated concrete5 -- concrete5 An issue was discovered in concrete5 /vendor/phpunit directory from your production deployments 2017-03-16 not yet calculated drupal -- drupal When adding a private file via the editor in Drupal 8.2.x before 8.2.7, the editor will not correctly check access for the file being attached, resulting in an access bypass. 2017-03-16 not yet calculated efs_software -- ftp_server Easy File Sharing FTP Server version 3.6 is vulnerable to a directory traversal vulnerability which allows an attacker to list and download any file from any folder outside the FTP root Directory. 2017-03-16 not yet calculated erlang -- erlang An issue was discovered in Erlang/OTP 18.x. Erlang's generation of compiled regular expressions is vulnerable to a heap overflow. Regular expressions using a malformed extpattern can indirectly specify an offset that is used as an array index.
This ordinal permits arbitrary regions within the erts_alloc arena to be both read and written to. 2017-03-18 not yet calculated fatek_automation_equipment -- plc_ethernet_module An issue was discovered in Fatek Automation PLC Ethernet Module. The affected Ether_cfg software configuration tool runs on the following Fatek PLCs: CBEH versions prior to V3.6 Build 170215, CBE versions prior to V3.6 Build 170215, CM55E versions prior to V3.6 Build 170215, and CM25E versions prior to V3.6 Build 170215.
A stack-based buffer overflow vulnerability has been identified, which may allow remote code execution or crash the affected device. 2017-03-16 not yet calculated getsimple_cms -- getsimple_cms GetSimple CMS 3.3.4 allows remote attackers to obtain sensitive information via a direct request to (1) data/users/.xml, (2) backups/users/.xml.bak, (3) data/other/authorization.xml, or (4) data/other/appid.xml. 2017-03-17 not yet calculated getsimple_cms -- getsimple_cms GetSimple CMS 3.3.4 allows remote attackers to obtain sensitive information via a direct request to (1) plugins/anonymous_data.php or (2) plugins/InnovationPlugin.php, which reveals the installation path in an error message. 2017-03-17 not yet calculated gnu_binutils -- readelf readelf in GNU Binutils 2.28 is vulnerable to a heap-based buffer over-read while processing corrupt RL78 binaries. The vulnerability can trigger program crashes. It may lead to an information leak as well. 2017-03-17 not yet calculated gnu_binutils -- readelf readelf in GNU Binutils 2.28 has a use-after-free (specifically read-after-free) error while processing multiple, relocated sections in an MSP430 binary.
This is caused by mishandling of an invalid symbol index, and mishandling of state across invocations. 2017-03-17 not yet calculated gnu_binutils -- readelf readelf in GNU Binutils 2.28 writes to illegal addresses while processing corrupt input files containing symbol-difference relocations, leading to a heap-based buffer overflow. 2017-03-17 not yet calculated imagemagick -- imagemagick coders/tiff.c in ImageMagick allows remote attackers to cause a denial of service (application crash) via vectors related to the 'identification of image.' 2017-03-17 not yet calculated imagemagick -- imagemagick distribute-cache.c in ImageMagick re-uses objects after they have been destroyed, which allows remote attackers to have unspecified impact via unspecified vectors. 2017-03-17 not yet calculated imagemagick -- imagemagick Memory leak in coders/rle.c in ImageMagick allows remote attackers to cause a denial of service (memory consumption) via a crafted rle file.
2017-03-17 not yet calculated intel_security_mcafee -- advanced_threat_defense Detection bypass vulnerability in Intel Security Advanced Threat Defense (ATD) 3.4.6 and earlier allows malware samples to bypass ATD detection via renaming the malware. 2017-03-14 not yet calculated intel_security_mcafee -- epolicy_orchestrator SQL injection vulnerability in core services in Intel Security McAfee ePolicy Orchestrator (ePO) 5.3.2 and earlier and 5.1.3 and earlier allows attackers to alter a SQL query, which can result in disclosure of information within the database or impersonation of an agent without authentication via a specially crafted HTTP post. 2017-03-14 not yet calculated intel_security_mcafee -- host_intrusion_prevention_services Authentication bypass vulnerability in McAfee Host Intrusion Prevention Services (HIPS) 8.0 Patch 7 and earlier allows authenticated users to manipulate the product's registry keys via specific conditions. 2017-03-14 not yet calculated intel_security_mcafee -- security_scan_plus Arbitrary command execution vulnerability in Intel Security McAfee Security Scan Plus (SSP) 3.11.469 and earlier allows authenticated users to gain elevated privileges via unspecified vectors. 2017-03-14 not yet calculated intel_security_mcafee -- security_scan Malicious file execution vulnerability in Intel Security McAfee Security Scan+ (MSS+) before 3.11.266.3 allows attackers to make the product momentarily vulnerable via executing preexisting specifically crafted malware during installation or uninstallation, but not during normal operation.
2017-03-14 not yet calculated intel_security_mcafee -- advanced_threat_defense SQL injection vulnerability in Intel Security Advanced Threat Defense (ATD) Linux 3.6.0 and earlier allows remote authenticated users to obtain product information via a crafted HTTP request parameter. 2017-03-14 not yet calculated intel_security_mcafee -- cloud_analysis_and_deconstructive_services Information disclosure vulnerability in McAfee (now Intel Security) Cloud Analysis and Deconstructive Services (CADS) 1.0.0.3x, 1.0.0.4d and earlier allows remote unauthenticated users to view, add, and remove users via a configuration error. 2017-03-14 not yet calculated intel_security_mcafee -- cloudav Malicious file execution vulnerability in Intel Security CloudAV (Beta) before 0.5.0.151.3 allows attackers to make the product momentarily vulnerable via executing preexisting specifically crafted malware during installation or uninstallation, but not during normal operation. 2017-03-14 not yet calculated intel_security_mcafee -- data_loss_prevention_endpoint Access control vulnerability in Intel Security Data Loss Prevention Endpoint (DLPe) 9.4.200 and 9.3.600 allows authenticated users with Read-Write-Execute permissions to inject hook DLLs into other processes via pages in the target process memory get.
2017-03-14 not yet calculated intel_security_mcafee -- epo_deep_command Unquoted executable path vulnerability in Client Management and Gateway components in McAfee (now Intel Security) ePO Deep Command (eDC) 2.2 and 2.1 allows authenticated users to execute a command of their choice via dropping a malicious file for the path. 2017-03-14 not yet calculated intel_security_mcafee -- mcafee_agent Man-in-the-middle (MitM) attack vulnerability in non-Mac OS agents in McAfee (now Intel Security) Agent (MA) 4.8.0 patch 2 and earlier allows attackers to make a McAfee Agent talk with another, possibly rogue, ePO server via McAfee Agent migration to another ePO server. 2017-03-14 not yet calculated intel_security_mcafee -- mcafee_application_control Application protections bypass vulnerability in Intel Security McAfee Application Control (MAC) 7.0 and earlier and Endpoint Security (ENS) 10.2 and earlier allows local users to bypass local security protection via a command-line utility. 2017-03-14 not yet calculated intel_security_mcafee -- mcafee_application_control Privilege escalation vulnerability in Intel Security McAfee Application Control (MAC) 7.0 and 6.x versions allows attackers to cause DoS, unexpected behavior, or potentially unauthorized code execution via an unauthorized use of IOCTL call. 2017-03-14 not yet calculated intel_security_mcafee -- mcafee_application_control Unauthorized execution of binary vulnerability in McAfee (now Intel Security) McAfee Application Control (MAC) 6.0.0 before hotfix 9726, 6.0.1 before hotfix 9068, 6.1.0 before hotfix 692, 6.1.1 before hotfix 399, 6.1.2 before hotfix 426, and 6.1.3 before hotfix 357 and earlier allows attackers to create a malformed Windows binary that is considered non-executable and is not protected through the whitelisting protection feature via a specific set of circumstances.
2017-03-14 not yet calculated intel_security_mcafee -- mcafee_email_gateway File extension filtering vulnerability in Intel Security McAfee Email Gateway (MEG) before 7.6.4 allows attackers to fail to identify the file name properly via scanning an email with a forged attached filename that uses a null byte within the filename extension. 2017-03-14 not yet calculated intel_security_mcafee -- saas_control_console A directory traversal vulnerability in the web application in McAfee (now Intel Security) SaaS Control Console (SCC) Platform 6.14 before patch 1070, and 6.15 before patch 1076 allows unauthenticated users to view contents of arbitrary system files that did not have file system level read access restrictions via a null-byte injection exploit. 2017-03-14 not yet calculated intel_security_mcafee -- security_scan_plus Privilege escalation vulnerability in Windows 7 and Windows 10 in McAfee Security Scan Plus (SSP) 3.11.376 allows attackers to load a replacement of the version.dll file via McAfee McUICnt.exe onto a Windows system. 2017-03-14 not yet calculated intel_security_mcafee -- vulnerability_manager Unsalted password vulnerability in the Enterprise Manager (web portal) component in Intel Security McAfee Vulnerability Manager (MVM) 7.5.8 and earlier allows attackers to more easily decrypt user passwords via brute force attacks against the database. 2017-03-14 not yet calculated intel_security_mcafee -- webadvisor Malicious file execution vulnerability in Intel Security WebAdvisor before 4.0.2, 4.0.1 and 3.7.2 allows attackers to make the product momentarily vulnerable via executing preexisting specifically crafted malware during installation or uninstallation, but not during normal operation. 2017-03-14 not yet calculated ioquake3 -- ioquake3 In ioquake3 before 2017-03-14, the auto-downloading feature has insufficient content restrictions.
This also affects Quake III Arena, OpenArena, OpenJK, iortcw, and other id Tech 3 (aka Quake 3 engine) forks. A malicious auto-downloaded file can trigger loading of crafted auto-downloaded files as native code DLLs. A malicious auto-downloaded file can contain configuration defaults that override the user's. Executable bytecode in a malicious auto-downloaded file can set configuration variables to values that will result in unwanted native code DLLs being loaded, resulting in sandbox escape. 2017-03-14 not yet calculated joomla! -- joomla!
Xrdp 0.9.1 calls the PAM function auth_start_session() in an incorrect location, leading to PAM session modules not being properly initialized, with a potential consequence of incorrect configurations or elevation of privileges, aka a pam_limits.so bypass. 2017-03-17 not yet calculated libcacard -- libcacard Memory leak in the vcard_apdu_new function in card_7816.c in libcacard before 2.5.3 allows local guest OS users to cause a denial of service (host memory consumption) via vectors related to allocating a new APDU object. 2017-03-15 not yet calculated libevent -- libevent The name_parse function in evdns.c in libevent before 2.1.6-beta allows remote attackers to have unspecified impact via vectors involving the label_len variable, which triggers an out-of-bounds stack read. 2017-03-15 not yet calculated libtiff -- libtiff LibTIFF allows remote attackers to cause a denial of service (memory consumption and crash) via a crafted tiff file.
2017-03-17 not yet calculated linux -- linux_containers lxc-user-nic in Linux Containers (LXC) allows local users with a lxc-usernet allocation to create network interfaces on the host and choose the name of those interfaces by leveraging lack of netns ownership check. 2017-03-14 not yet calculated linux -- linux_kernel The keyring_search_aux function in security/keys/keyring.c in the Linux kernel through 3.14.79 allows local users to cause a denial of service (NULL pointer dereference and OOPS) via a request_key system call for the 'dead' type. 2017-03-16 not yet calculated magnicomp -- magnicomp A Local Privilege Escalation Vulnerability in MagniComp's Sysinfo before 10-H64 for Linux and UNIX platforms could allow a local attacker to gain elevated privileges. Parts of SysInfo require setuid-to-root access in order to access restricted system files and make restricted kernel calls. This access could be exploited by a local attacker to gain a root shell prompt using the right combination of environment variables and command line arguments. 2017-03-14 not yet calculated mantisbt -- mantisbt An XSS vulnerability in the MantisBT Source Integration Plugin (before 2.0.2) search result page allows an attacker to inject arbitrary HTML or JavaScript (if MantisBT's CSP settings permit it) by crafting any valid parameter. 2017-03-17 not yet calculated mcafee_intel_security -- advanced_threat_defense Sandbox detection evasion vulnerability in hardware appliances in McAfee (now Intel Security) Advanced Threat Defense (MATD) 3.4.2.32 and earlier allows attackers to detect the sandbox environment, then bypass proper malware detection resulting in failure to detect a malware file (false-negative) via specially crafted malware.
2017-03-14 not yet calculated microsoft -- exchange_outlook_web_access Cross-site scripting (XSS) vulnerability in Microsoft Exchange Outlook Web Access (OWA) allows remote attackers to inject arbitrary web script or HTML via a crafted email or chat client, aka 'Microsoft Exchange Server Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- internet_explorer Microsoft Internet Explorer 10 and 11 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka 'Internet Explorer Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0037 and CVE-2017-0149.
2017-03-16 not yet calculated microsoft -- internet_explorer The scripting engine in Microsoft Internet Explorer 9 through 11 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka 'Scripting Engine Memory Corruption Vulnerability.' This vulnerability is different from that described in CVE-2017-0040. 2017-03-16 not yet calculated microsoft -- lync Microsoft Lync for Mac 2011 fails to properly validate certificates, allowing remote attackers to alter server-client communications, aka 'Microsoft Lync for Mac Certificate Validation Vulnerability.' 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers.
These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers.
These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, and CVE-2017-0150. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system.
An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers.
These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers.
These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system.
An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system.
An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user.
An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151. 2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers.
These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0137, CVE-2017-0138, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_browsers A remote code execution vulnerability exists in the way affected Microsoft scripting engines render when handling objects in memory in Microsoft browsers. These vulnerabilities could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. If the current user is logged on with administrative user rights, an attacker who successfully exploited the vulnerability could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability is different from those described in CVE-2017-0010, CVE-2017-0015, CVE-2017-0032, CVE-2017-0035, CVE-2017-0067, CVE-2017-0070, CVE-2017-0071, CVE-2017-0094, CVE-2017-0131, CVE-2017-0132, CVE-2017-0133, CVE-2017-0134, CVE-2017-0136, CVE-2017-0138, CVE-2017-0141, CVE-2017-0150, and CVE-2017-0151.
2017-03-16 not yet calculated microsoft -- microsoft_edge Microsoft Edge allows remote attackers to bypass the Same Origin Policy for HTML elements in other browser windows, aka 'Microsoft Edge Security Feature Bypass Vulnerability.' This vulnerability is different from those described in CVE-2017-0135 and CVE-2017-0140.
2017-03-16 not yet calculated microsoft -- sharepoint Microsoft SharePoint Server fails to sanitize crafted web requests, allowing remote attackers to run cross-script in local security context, aka 'Microsoft SharePoint XSS Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 10 Gold, 1511, and 1607 and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0056, CVE-2017-0078, CVE-2017-0079, CVE-2017-0081, and CVE-2017-0082. 2017-03-16 not yet calculated microsoft -- windows A DCOM object in Helppane.exe in Microsoft Windows 7 SP1; Windows Server 2008 R2; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows local users to gain privileges via a crafted application, aka 'Windows HelpPane Elevation of Privilege Vulnerability.'
2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows 10 Gold, 1511, and 1607 and Windows Server 2016 does not properly validate vSMB packet data, which allows attackers to execute arbitrary code on a target OS, aka 'Hyper-V vSMB Remote Code Execution Vulnerability.' This vulnerability is different from that described in CVE-2017-0021.
2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0078, CVE-2017-0079, CVE-2017-0080, CVE-2017-0081, CVE-2017-0082. 2017-03-16 not yet calculated microsoft -- windows The iSNS Server service in Microsoft Windows Server 2008 SP2 and R2, Windows Server 2012 Gold and R2, and Windows Server 2016 allows remote attackers to issue malicious requests via an integer overflow, aka 'iSNS Server Memory Corruption Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows The kernel API in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, and Windows Server 2012 mishandles registry objects in memory, which allows local users to gain privileges via a crafted application, aka 'Windows Registry Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Word 2007 SP3, Office 2010 SP2, Word 2010 SP2, Word for Mac 2011, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2, and Office Web Apps 2010 SP2 allow remote attackers to obtain sensitive information from out-of-bound memory via a crafted Office document, aka 'Microsoft Office Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Excel 2016, Excel 2010 SP2, Excel 2013 RT SP1, and Office Web Apps Server 2013 SP1 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0019, CVE-2017-0030, CVE-2017-0031, CVE-2017-0052, and CVE-2017-0053.
2017-03-16 not yet calculated microsoft -- windows Microsoft Internet Information Server (IIS) in Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to perform cross-site scripting and run script with local user privileges via a crafted request, aka 'Microsoft IIS Server XSS Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 let attackers with access to targets systems gain privileges when Windows fails to properly validate buffer lengths, aka 'Windows Elevation of Privilege Vulnerability.'
2017-03-16 not yet calculated microsoft -- windows Microsoft Excel 2007 SP3, Excel 2010 SP2, Excel 2013 RT SP1, Excel 2016, Office Compatibility Pack SP3, and Excel Services on SharePoint Server 2013 SP1 allow remote attackers to obtain sensitive information from process memory via a crafted Office document, aka 'Microsoft Office Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka 'Hyper-V Denial of Service Vulnerability.' This vulnerability is different from those described in CVE-2017-0074, CVE-2017-0076, CVE-2017-0097, and CVE-2017-0099. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and 2008 R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka 'Hyper-V Denial of Service Vulnerability.' This vulnerability is different from those described in CVE-2017-0098, CVE-2017-0074, CVE-2017-0076, and CVE-2017-0097. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and 2008 R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 and R2; Windows 10, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka 'Hyper-V Denial of Service Vulnerability.' This vulnerability is different from those described in CVE-2017-0098, CVE-2017-0074, CVE-2017-0076, and CVE-2017-0099.
2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0056, CVE-2017-0078, CVE-2017-0079, CVE-2017-0080, CVE-2017-0082. 2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Windows GDI+ Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0060 and CVE-2017-0062.
2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and 2008 R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 and R2; Windows 10, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka 'Hyper-V Denial of Service Vulnerability.' This vulnerability is different from those described in CVE-2017-0098, CVE-2017-0076, CVE-2017-0097, and CVE-2017-0099. 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0056, CVE-2017-0079, CVE-2017-0080, CVE-2017-0081, CVE-2017-0082. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and 2008 R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 and R2; Windows 10, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka 'Hyper-V Denial of Service Vulnerability.'
This vulnerability is different from those described in CVE-2017-0098, CVE-2017-0074, CVE-2017-0097, and CVE-2017-0099. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows guest OS users to execute arbitrary code on the host OS via a crafted application, aka 'Hyper-V Remote Code Execution Vulnerability.' This vulnerability is different from that described in CVE-2017-0109. 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Windows 8.1; Windows Server 2012 R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0056, CVE-2017-0078, CVE-2017-0080, CVE-2017-0081, and CVE-2017-0082.
2017-03-16 not yet calculated microsoft -- windows DNS client in Microsoft Windows 8.1; Windows Server 2012 R2, Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 fails to properly process DNS queries, which allows remote attackers to obtain sensitive information via (1) convincing a workstation user to visit an untrusted webpage or (2) tricking a server into sending a DNS query to a malicious DNS server, aka 'Windows DNS Query Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows 10 1607 and Windows Server 2016 does not properly validate vSMB packet data, which allows attackers to execute arbitrary code on a target OS, aka 'Hyper-V System Data Structure Vulnerability.' This vulnerability is different from that described in CVE-2017-0095. 2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'GDI+ Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0060 and CVE-2017-0073.
2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Transaction Manager in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Windows Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows The Color Management Module (ICM32.dll) memory handling functionality in Windows Vista SP2; Windows Server 2008 SP2 and R2; and Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to bypass ASLR and execute code in combination with another vulnerability through a crafted website, aka 'Microsoft Color Management Information Disclosure Vulnerability.'
This vulnerability is different from that described in CVE-2017-0061. 2017-03-16 not yet calculated microsoft -- windows The Color Management Module (ICM32.dll) memory handling functionality in Windows Vista SP2, Windows Server 2008 SP2 and R2, and Windows 7 SP1 allows remote attackers to bypass ASLR and execute code in combination with another vulnerability through a crafted website, aka 'Microsoft Color Management Information Disclosure Vulnerability.' This vulnerability is different from that described in CVE-2017-0063. 2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'GDI+ Information Disclosure Vulnerability.' This vulnerability is different from those described in CVE-2017-0060 and CVE-2017-0062.
2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 10 Gold and 1511 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0026, CVE-2017-0056, CVE-2017-0078, CVE-2017-0079, CVE-2017-0080, and CVE-2017-0081. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1, Windows Server 2012 Gold and R2; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows guest OS users to obtain sensitive information from host OS memory via a crafted application, aka 'Hyper-V Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Office 2010 SP2, Office Compatibility Pack SP3, Office Web Apps Server 2010 SP2, Word 2007 SP3, Word 2010 SP2, and Word Automation Services on SharePoint Server 2010 SP2 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.'
This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0019, CVE-2017-0020, CVE-2017-0031, CVE-2017-0052, and CVE-2017-0053. 2017-03-16 not yet calculated microsoft -- windows Microsoft Windows Vista SP2 and Server 2008 SP2 mishandle dynamic link library (DLL) loading, which allows local users to gain privileges via a crafted application, aka 'Library Loading Input Validation Remote Code Execution Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Office 2010 SP2, Word 2010 SP2, Word 2013 RT SP1, and Word 2016 allow remote attackers to cause a denial of service (application hang) via a crafted Office document, aka 'Microsoft Office Denial of Service Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows The Windows Graphics Component in Microsoft Office 2007 SP3; 2010 SP2; and Word Viewer; Skype for Business 2016; Lync 2013 SP1; Lync 2010; Live Meeting 2007; Silverlight 5; Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; and Windows 7 SP1 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Graphics Component Remote Code Execution Vulnerability.' This vulnerability is different from that described in CVE-2017-0014. 2017-03-16 not yet calculated microsoft -- windows Active Directory Federation Services in Microsoft Windows 10 1607, Windows Server 2008 SP2 and R2 SP1, Windows Server 2012 Gold and R2, and Windows Server 2016 allows local users to obtain sensitive information via a crafted application, aka 'Microsoft Active Directory Federation Services Information Disclosure Vulnerability.'
2017-03-16 not yet calculated microsoft -- windows Windows Media Player in Microsoft Windows 8.1; Windows Server 2012 R2; Windows RT 8.1; Windows 7 SP1; Windows 2008 SP2 and R2 SP1, Windows Server 2016; Windows Vista SP2; and Windows 10 Gold, 1511, and 1607 allows remote attackers to obtain sensitive information via a crafted web site, aka 'Windows Media Player Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Office 2010 SP2, Office Compatibility Pack SP3, Word 2007 SP3, and Word 2010 SP2 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.'
This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0019, CVE-2017-0020, CVE-2017-0030, CVE-2017-0052, and CVE-2017-0053. 2017-03-16 not yet calculated microsoft -- windows Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, and 1607, and Windows Server 2016 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Windows Uniscribe Remote Code Execution Vulnerability.' This vulnerability is different from those described in CVE-2017-0072, CVE-2017-0083, CVE-2017-0086, CVE-2017-0087, CVE-2017-0088, CVE-2017-0089, and CVE-2017-0090. 2017-03-16 not yet calculated microsoft -- windows Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, and 1607, and Windows Server 2016 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.' CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0119, CVE-2017-0120, CVE-2017-0121, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128.
2017-03-16 not yet calculated microsoft -- windows The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to obtain sensitive information from process memory via a crafted packets, aka 'Windows SMB Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft XML Core Services (MSXML) in Windows 10 Gold, 1511, and 1607; Windows 7 SP1; Windows 8.1; Windows RT 8.1; Windows Server 2008 SP2 and R2 SP1; Windows Server 2012 Gold and R2; Windows Server 2016; and Windows Vista SP2 improperly handles objects in memory, allowing attackers to test for files on disk via a crafted web site, aka 'Microsoft XML Information Disclosure Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Internet Explorer 11 on Windows 10, 1511, and 1606 and Windows Server 2016 does not enforce cross-domain policies, allowing attackers to access information from one domain and inject it into another via a crafted application, aka, 'Internet Explorer Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Uniscribe in Microsoft Windows Vista SP2, Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, and 1607, and Windows Server 2016 allows remote attackers to obtain sensitive information from process memory via a crafted web site, aka 'Uniscribe Information Disclosure Vulnerability.'
CVE-2017-0085, CVE-2017-0091, CVE-2017-0092, CVE-2017-0111, CVE-2017-0112, CVE-2017-0113, CVE-2017-0114, CVE-2017-0115, CVE-2017-0116, CVE-2017-0117, CVE-2017-0118, CVE-2017-0119, CVE-2017-0120, CVE-2017-0122, CVE-2017-0123, CVE-2017-0124, CVE-2017-0125, CVE-2017-0126, CVE-2017-0127, and CVE-2017-0128. 2017-03-16 not yet calculated microsoft -- windows Microsoft Office Compatibility Pack SP3, Excel 2007 SP3, Excel Viewer, and Excel Services on SharePoint Server 2007 SP3 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0019, CVE-2017-0020, CVE-2017-0030, CVE-2017-0031, and CVE-2017-0053. 2017-03-16 not yet calculated microsoft -- windows Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows guest OS users to execute arbitrary code on the host OS via a crafted application, aka 'Hyper-V Remote Code Execution Vulnerability.' This vulnerability is different from that described in CVE-2017-0075. 2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows local users to gain privileges via a crafted application, aka 'Windows GDI Elevation of Privilege Vulnerability.'
This vulnerability is different from those described in CVE-2017-0001, CVE-2017-0025, and CVE-2017-0047. 2017-03-16 not yet calculated microsoft -- windows Microsoft Excel 2007 SP3, Office Compatibility Pack SP3, Excel Viewer, and Excel Services on SharePoint Server 2007 SP3 allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0019, CVE-2017-0020, CVE-2017-0030, CVE-2017-0031, CVE-2017-0052, and CVE-2017-0053.
2017-03-16 not yet calculated microsoft -- windows Microsoft Windows 10 Gold, 1511, and 1607; Windows 8.1; Windows RT 8.1; Windows Server 2012 R2, and Windows Server 2016 do not properly handle certain requests in SMBv2 and SMBv3 packets, which allows remote attackers to execute arbitrary code via a crafted SMBv2 or SMBv3 packet to the Server service, aka 'SMBv2/SMBv3 Null Dereference Denial of Service Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Microsoft Word 2016 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.' This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0020, CVE-2017-0030, CVE-2017-0031, CVE-2017-0052, and CVE-2017-0053. 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 10 1607 and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.'
This vulnerability is different from those described in CVE-2017-0026, CVE-2017-0056, CVE-2017-0078, CVE-2017-0079, CVE-2017-0080, CVE-2017-0081, and CVE-2017-0082. 2017-03-16 not yet calculated microsoft -- windows Microsoft Office 2010 SP2, Office Compatibility Pack SP3, Word 2007 SP3, Word 2010 SP2, Word 2013 SP1, Word 2013 R2 SP1, Word 2016, and Word Viewer allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted document, aka 'Microsoft Office Memory Corruption Vulnerability.'
This vulnerability is different from those described in CVE-2017-0006, CVE-2017-0019, CVE-2017-0020, CVE-2017-0030, CVE-2017-0031, and CVE-2017-0052. 2017-03-16 not yet calculated microsoft -- windows The Windows Graphics Component in Microsoft Office 2010 SP2; Windows Server 2008 R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to execute arbitrary code via a crafted web site, aka 'Windows Graphics Component Remote Code Execution Vulnerability.' This vulnerability is different from that described in CVE-2017-0108. 2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows local users to gain privileges via a crafted application, aka 'Windows GDI Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0005, CVE-2017-0025, and CVE-2017-0047. 2017-03-16 not yet calculated microsoft -- windows Windows DVD Maker in Windows 7 SP1, Windows Server 2008 SP2 and R2 SP1, and Windows Vista SP2 does not properly parse crafted.msdvd files, which allows attackers to obtain information to compromise a target system, aka 'Windows DVD Maker Cross-Site Request Forgery Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows Device Guard in Microsoft Windows 10 Gold, 1511, 1607, and Windows Server 2016 allows remote attackers to modify PowerShell script without invalidating associated signatures, aka 'PowerShell Security Feature Bypass Vulnerability.'
2017-03-16 not yet calculated microsoft -- windows The Graphics Device Interface (GDI) in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607 allows local users to gain privileges via a crafted application, aka 'Windows GDI Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0001, CVE-2017-0005 and CVE-2017-0025. 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows 10 Gold, 1511, and 1607 and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.' This vulnerability is different from those described in CVE-2017-0024, CVE-2017-0056, CVE-2017-0078, CVE-2017-0079, CVE-2017-0080, CVE-2017-0081, and CVE-2017-0082.
2017-03-16 not yet calculated microsoft -- windows The kernel API in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7; Windows 8; Windows 10 Gold, 1511, and 1607; Windows RT 8.1; Windows Server 2012 Gold and R2; and Windows Server 2016 does not properly enforce permissions, which allows local users to spoof processes, spoof inter-process communication, or cause a denial of service via a crafted application, aka 'Windows Kernel Elevation of Privilege Vulnerability.' 2017-03-16 not yet calculated microsoft -- windows The kernel-mode drivers in Microsoft Windows Vista; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allow local users to gain privileges via a crafted application, aka 'Win32k Elevation of Privilege Vulnerability.'
This vulnerability is different from those described in CVE-2017-0001, CVE-2017-0005, and CVE-2017-0047. 2017-03-16 not yet calculated netgear -- dgn2200_router Cross-site request forgery (CSRF) vulnerability in NETGEAR DGN2200 routers with firmware 10.0.0.20 through 10.0.0.50 allows remote attackers to hijack the authentication of users for requests that perform DNS lookups via the host_name parameter to dnslookup.cgi. NOTE: this issue can be combined with CVE-2017-6334 to execute arbitrary code remotely. 2017-03-15 not yet calculated open.gl -- open.gl An issue was discovered in Open.GL before 2017-03-13. The vulnerability exists due to insufficient filtration of user-supplied data (content) passed to the 'Open.GL-master/index.php' URL. An attacker could execute arbitrary HTML and script code in a browser in the context of the vulnerable website.
2017-03-14 not yet calculated pluck_cms -- pluck_cms Pluck CMS 4.7.2 allows remote attackers to obtain sensitive information by (1) changing 'PHPSESSIS' to an array; (2) adding non-aplhanumeric chars to 'PHPSESSID'; (3) changing the image parameter to array; or (4) changing the image parameter to a string, which reveals the installation path in an error message. 2017-03-17 not yet calculated pluck_cms -- pluck_cms Pluck CMS 4.7.2 allows remote attackers to execute arbitrary code via the blog form feature.
2017-03-17 not yet calculated pluck_cms -- pluck_cms Cross-site scripting (XSS) vulnerability in TinyMCE in Pluck CMS 4.7.2 allows remote authenticated users to inject arbitrary web script or HTML via the 'edit HTML source' option. 2017-03-17 not yet calculated podofo -- podofo Heap-based buffer overflow in the PdfParser::ReadXRefSubsection function in base/PdfParser.cpp in PoDoFo allows attackers to have unspecified impact via vectors related to m_offsets.size. 2017-03-16 not yet calculated qdpm -- qdpm Information disclosure issue in qdPM 8.3 allows remote attackers to obtain sensitive information via a direct request to (1) core/config/databases.yml, (2) core/log/qdPM_prod.log, or (3) core/apps/qdPM/config/settings.yml.
2017-03-17 not yet calculated qdpm -- qdpm Unrestricted file upload vulnerability in the (1) myAccount, (2) projects, (3) tasks, (4) tickets, (5) discussions, (6) reports, and (7) scheduler pages in qdPM 8.3 allows remote attackers to execute arbitrary code by uploading a file with an executable extension, then accessing it via a direct request to the file in uploads/attachments/ or uploads/users/. 2017-03-17 not yet calculated qdpm -- qdpm qdPM 8.3 allows remote attackers to obtain sensitive information via invalid ID value to index.php/users/info/id/[ID], which reveals the installation path in an error message. 2017-03-17 not yet calculated qdpm -- qdpm Multiple cross-site scripting (XSS) vulnerabilities in qdPM 8.3 allow remote attackers to inject arbitrary web script or HTML via the (1) search[keywords] parameter to index.php/users page; the (2) 'Name of application' on index.php/configuration; (3) a new project name on index.php/projects; (4) the task name on index.php/tasks; (5) ticket name on index.php/tickets; (6) discussion name on index.php/discussions; (7) report name on index.php/projectReports; or (8) event name on index.php/scheduler/personal. 2017-03-17 not yet calculated sawmill_enterprise -- sawmill_enterprise Sawmill Enterprise 8.7.9 allows remote attackers to gain login access by leveraging knowledge of a password hash. 2017-03-15 not yet calculated shimmie -- shimmie An issue was discovered in Shimmie.
• • • Getting Started and General Information • • • • • • • • • • Configuring Access Lists • • • • • • • • • Configuring IP Routing • • • • • • • • • Configuring NAT • • • • • • • Configuring High Availability • • • • Configuring Access Control • • • • • • Configuring Application Layer Procotol Inspection • • • • • • Configuring Unified Communications • • • • • • Configuring Advanced Connection Settings • • • • • • • • • Configuring Applications on SSMs and SSCs • • • • Configuring VPN • • • • • • • • • • • • • • Monitoring • • • • • System Administration • • • Reference • • • • • Search. Managing Feature Licenses A license specifies the options that are enabled on a given ASA. It is represented by an activation key which is a 160-bit (5 32-bit words or 20 bytes) value. This value encodes the serial number (an 11 character string) and the enabled features. This chapter describes how to obtain an activation key and activate it.
It also describes the available licenses for each model. This chapter includes the following sections: • • • • • • • • • Supported Feature Licenses Per Model This section describes the licenses available for each model as well as important notes about licenses. This section includes the following topics: • • • Licenses Per Model This section lists the feature licenses available for each model: • ASA 5505, • ASA 5510, • ASA 5520, • ASA 5540, • ASA 5550, • ASA 5580, • ASA 5585-X, Items that are in italics are separate, optional licenses with which that you can replace the Base or Security Plus license. You can mix and match licenses, for example, the 10 security context license plus the Strong Encryption license; or the 500 Clientless SSL VPN license plus the GTP/GPRS license; or all four licenses together. Table 3-1 ASA 5505 Adaptive Security Appliance License Features ASA 5505 Base License Security Plus Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Disabled Optional temporary license: Available Firewall Conns, Concurrent 10 K 25 K GTP/GPRS No support No support Unified Comm. Sessions 2 Optional license: 24 2 Optional license: 24 VPN Licenses Adv. Endpoint Assessment Disabled Optional license: Available Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 2 Optional Permanent licenses: 10 25 10 25 IPSec VPN (sessions) 10 (max.
25 combined IPSec and SSL VPN) 25 (max. 25 combined IPSec and SSL VPN) VPN Load Balancing No support No support General Licenses Encryption Base (DES) Opt. Lic.: Strong (3DES/AES) Base (DES) Opt.
Lic.: Strong (3DES/AES) Failover No support Active/Standby (no stateful failover) Security Contexts No support No support Users, concurrent 10 Optional licenses: 10 Optional licenses: 50 Unlimited 50 Unlimited VLANs/Zones, Maximum 3 (2 regular zones and 1 restricted zone) 20 VLAN Trunk, Maximum No support 8 trunks See the 'License Notes' section. See the 'VPN License and Feature Compatibility' section. In routed mode, hosts on the inside (Business and Home VLANs) count towards the limit when they communicate with the outside (Internet VLAN), including when the inside initiates a connection to the outside as well as when the outside initiates a connection to the inside. Note that even when the outside initiates a connection to the inside, outside hosts are not counted towards the limit; only the inside hosts count. Hosts that initiate traffic between Business and Home are also not counted towards the limit.
The interface associated with the default route is considered to be the outside Internet interface. If there is no default route, hosts on all interfaces are counted toward the limit.
In transparent mode, the interface with the lowest number of hosts is counted towards the host limit. See the show local-host command to view host limits. For a 10-user license, the max. DHCP clients is 32. For 50 users, the max.
For unlimited users, the max. Is 250, which is the max. For other models.
Table 3-2 ASA 5510 Adaptive Security Appliance License Features ASA 5510 Base License Security Plus Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Disabled Optional temporary license: Available Firewall Conns, Concurrent 50 K 130 K GTP/GPRS No support No support Unified Comm. Sessions 2 Optional licenses: 2 Optional licenses: 24 50 100 24 50 100 VPN Licenses Adv. Endpoint Assessment Disabled Optional license: Available Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 2 Optional Permanent licenses: 10 25 50 100 250 10 25 50 100 250 Optional Shared licenses: Participant or Server. For the Server, these licenses are available: Optional Shared licenses: Participant or Server. For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX license: 250 Optional FLEX license: 250 IPSec VPN (sessions) 250 (max.
250 combined IPSec and SSL VPN) 250 (max. 250 combined IPSec and SSL VPN) VPN Load Balancing No support Supported General Licenses Encryption Base (DES) Opt. Lic.: Strong (3DES/AES) Base (DES) Opt.
Lic.: Strong (3DES/AES) Failover No support Active/Standby or Active/Active Interface Speed All: Fast Ethernet Ethernet 0/0 and 0/1: Gigabit Ethernet Ethernet 0/2, 0/3, and 0/4: Fast Ethernet Security Contexts No support 2 Optional licenses: 5 VLANs, Maximum 50 100 See the 'License Notes' section. See the 'VPN License and Feature Compatibility' section. Although the Ethernet 0/0 and 0/1 ports are Gigabit Ethernet, they are still identified as 'Ethernet' in the software. Table 3-3 ASA 5520 Adaptive Security Appliance License Features ASA 5520 Base License Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Firewall Conns, Concurrent 280 K GTP/GPRS Disabled Optional license: Available Unified Communications Proxy Sessions 2 Optional licenses: 24 50 100 250 500 750 1000 VPN Licenses Adv. Endpoint Assessment Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 10 25 50 100 250 500 750 Optional Shared licenses: Participant or Server. For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX licenses: 250 750 IPSec VPN (sessions) 750 (max.
750 combined IPSec and SSL VPN) VPN Load Balancing Supported General Licenses Encryption Base (DES) Optional license: Strong (3DES/AES) Failover Active/Standby or Active/Active Security Contexts 2 Optional licenses: 5 10 20 VLANs, Maximum 150 See the 'License Notes' section. See the 'VPN License and Feature Compatibility' section. Table 3-4 ASA 5540 Adaptive Security Appliance License Features ASA 5540 Base License Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Firewall Conns, Concurrent 400 K GTP/GPRS Disabled Optional license: Available Unified Communications Proxy Sessions 2 Optional licenses: 24 50 100 250 500 750 1000 2000 VPN Licenses Adv.
Endpoint Assessment Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 10 25 50 100 250 500 750 1000 2500 Optional Shared licenses: Participant or Server. For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX licenses: 250 750 1000 2500 IPSec VPN (sessions) 5000 (max. 5000 combined IPSec and SSL VPN) VPN Load Balancing Supported General Licenses Encryption Base (DES) Optional license: Strong (3DES/AES) Failover Active/Standby or Active/Active Security Contexts 2 Optional licenses: 5 10 20 50 VLANs, Maximum 200 See the 'License Notes' section.
See the 'VPN License and Feature Compatibility' section. Table 3-5 ASA 5550 Adaptive Security Appliance License Features ASA 5550 Base License Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Firewall Conns, Concurrent 650 K GTP/GPRS Disabled Optional license: Available Unified Communications Proxy Sessions 2 Optional licenses: 24 50 100 250 500 750 1000 2000 3000 VPN Licenses Adv. Endpoint Assessment Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 10 25 50 100 250 500 750 1000 2500 5000 Optional Shared licenses: Participant or Server. For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX licenses: 250 750 1000 2500 5000 IPSec VPN (sessions) 5000 (max. 5000 combined IPSec and SSL VPN) VPN Load Balancing Supported General Licenses Encryption Base (DES) Optional license: Strong (3DES/AES) Failover Active/Standby or Active/Active Security Contexts 2 Optional licenses: 5 10 20 50 VLANs, Maximum 250 See the 'License Notes' section.
See the 'VPN License and Feature Compatibility' section. Table 3-6 ASA 5580 Adaptive Security Appliance License Features ASA 5580 Base License Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Firewall Conns, Concurrent 5580-20: 1,000 K 5580-40: 2,000 K GTP/GPRS Disabled Optional license: Available Unified Communications Proxy Sessions 2 Optional licenses: 24 50 100 250 500 750 1000 2000 3000 5000 10000 VPN Licenses Adv. Endpoint Assessment Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 10 25 50 100 250 500 750 1000 2500 5000 Optional Shared licenses: Participant or Server.
For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX licenses: 250 750 1000 2500 5000 IPSec VPN (sessions) 5000 (max. 5000 combined IPSec and SSL VPN) VPN Load Balancing Supported General Licenses Encryption Base (DES) Optional license: Strong (3DES/AES) Failover Active/Standby or Active/Active Security Contexts 2 Optional licenses: 5 10 20 50 VLANs, Maximum 250 See the 'License Notes' section. With the 10,000-session license, the total combined sessions can be 10,000, but the maximum number of Phone Proxy sessions is 5000. See the 'VPN License and Feature Compatibility' section. Table 3-7 ASA 5585-X Adaptive Security Appliance License Features ASA 5585-X Base License Firewall Licenses Botnet Traffic Filter Disabled Optional temporary license: Available Firewall Conns, Concurrent 5585-X with SSP-10: 750 K 5585-X with SSP-20: 1,000 K 5585-X with SSP-40: 2,000 K 5585-X with SSP-60: 2,000 K GTP/GPRS Disabled Optional license: Available Unified Communications Proxy Sessions 2 Optional licenses: 24 50 100 250 500 750 1000 2000 3000 5000 10000 VPN Licenses Adv.
Endpoint Assessment Disabled Optional license: Available AnyConnect Essentials Disabled Optional license: Available AnyConnect Mobile Disabled Optional license: Available AnyConnect Premium SSL VPN (sessions) 2 Optional Permanent licenses: 10 25 50 100 250 500 750 1000 2500 5000 10000 Optional Shared licenses: Participant or Server. For the Server, these licenses are available: 500-50,000 in increments of 500 50,000-545,000 in increments of 1000 Optional FLEX licenses: 250 750 1000 2500 5000 IPSec VPN (sessions) 5000 (max. 5000 combined IPSec and SSL VPN) VPN Load Balancing Supported General Licenses Encryption Base (DES) Optional license: Strong (3DES/AES) Failover Active/Standby or Active/Active 10 GE I/O for SSP-10 and SSP-20 Disabled; fiber ifcs run at 1 GE Optional license: Available; fiber ifcs run at 10 GE Security Contexts 2 Optional licenses: 5 10 20 50 VLANs, Maximum 250 See the 'License Notes' section. With the 10,000-session license, the total combined sessions can be 10,000, but the maximum number of Phone Proxy sessions is 5000.
See the 'VPN License and Feature Compatibility' section. The ASA 5585-X with SSP-40 and -60 support 10-Gigabit Ethernet speeds by default.
License Notes lists footnotes for the tables in the. Table 3-8 License Notes License Notes Active/Active failover You cannot use Active/Active failover and VPN; if you want to use VPN, use Active/Standby failover.
AnyConnect Essentials This license enables AnyConnect VPN client access to the adaptive security appliance. This license does not support deploy browser-based SSL VPN access or Cisco Secure Desktop. For these features, activate an AnyConnect Premium SSL VPN license instead of the AnyConnect Essentials license. Note With the AnyConnect Essentials license, VPN users can use a Web browser to log in, and download and start (WebLaunch) the AnyConnect client. The AnyConnect client software offers the same set of client features, whether it is enabled by this license or an AnyConnect Premium SSL VPN license. The AnyConnect Essentials license cannot be active at the same time as the following licenses on a given adaptive security appliance: AnyConnect Premium SSL VPN license (all types) or the Advanced Endpoint Assessment license.
You can, however, run AnyConnect Essentials and AnyConnect Premium SSL VPN licenses on different adaptive security appliances in the same network. By default, the ASA uses the AnyConnect Essentials license, but you can disable it to use other licenses by using the no anyconnect-essentials command. AnyConnect Mobile This license provides access to the AnyConnect Client for touch-screen mobile devices running Windows Mobile 5.0, 6.0, and 6.1. We recommend using this license if you want to support mobile access to AnyConnect 2.3 and later versions. This license requires activation of one of the following licenses to specify the total number SSL VPN sessions permitted: AnyConnect Essentials or AnyConnect Premium SSL VPN.
AnyConnect Premium SSL VPN Shared A shared license lets the ASA act as a shared license server for multiple client ASAs. The shared license pool is large, but the maximum number of sessions used by each individual ASA cannot exceed the maximum number listed for permanent licenses. Botnet Traffic Filter Requires a Strong Encryption (3DES/AES) License to download the dynamic database. Encryption The DES license cannot be disabled. If you have the 3DES license installed, DES is still available. To prevent the use of DES when you want to only use strong encryption, be sure to configure any relevant commands to use only string encryption.
Combined IPSec and SSL VPN sessions • Although the maximum IPSec and SSL VPN sessions add up to more than the maximum VPN sessions, the combined sessions should not exceed the VPN session limit. If you exceed the maximum VPN sessions, you can overload the ASA, so be sure to size your network appropriately.
• If you start a clientless SSL VPN session and then start an AnyConnect client session from the portal, 1 session is used in total. However, if you start the AnyConnect client first (from a standalone client, for example) and then log into the clientless SSL VPN portal, then 2 sessions are used. Unified Communications Proxy sessions Phone Proxy, Mobility Advantage Proxy, Presence Federation Proxy, and TLS Proxy are all licensed under the UC Proxy umbrella, and can be mixed and matched. For example, if you configure a phone with a primary and backup Cisco Unified Communications Manager, there are 2 TLS/SRTP connections, so 2 UC Proxy sessions are used. Note In Version 8.2(2) and later, Mobility Advantage Proxy no longer requires the UC Proxy license.
VPN load balancing Requires a Strong Encryption (3DES/AES) License. VPN License and Feature Compatibility shows how the VPN licenses and features can combine. Table 3-9 VPN License and Feature Compatibility Supported with: Enable one of the following licenses: AnyConnect Essentials AnyConnect Premium SSL VPN AnyConnect Mobile Yes Yes Advanced Endpoint Assessment No Yes AnyConnect Premium SSL VPN Shared No Yes Client-based SSL VPN Yes Yes Browser-based (clientless) SSL VPN No Yes IPsec VPN Yes Yes VPN Load Balancing Yes Yes Cisco Secure Desktop No Yes You can only have one license type active, either the AnyConnect Essentials license or the AnyConnect Premium license. By default, the ASA includes an AnyConnect Premium license for 2 sessions.
If you install the AnyConnect Essentials license, then it is used by default. See the no anyconnect-essentials command to enable the Premium license instead. Information About Feature Licenses A license specifies the options that are enabled on a given ASA.
It is represented by an activation key that is a 160-bit (5 32-bit words or 20 bytes) value. This value encodes the serial number (an 11 character string) and the enabled features. This section includes the following topics: • • • • Preinstalled License By default, your ASA ships with a license already installed. This license might be the Base License, to which you want to add more licenses, or it might already have all of your licenses installed, depending on what you ordered and what your vendor installed for you. See the section to determine which licenses you have installed.
Temporary, VPN Flex, and Evaluation Licenses In addition to permanent licenses, you can purchase a temporary license or receive an evaluation license that has a time-limit. For example, you might buy a VPN Flex license to handle short-term surges in the number of concurrent SSL VPN users, or you might order a Botnet Traffic Filter temporary license that is valid for 1 year. This section includes the following topics: • • • How the Temporary License Timer Works • The timer for the temporary license starts counting down when you activate it on the ASA.
• If you stop using the temporary license before it times out, for example you activate a permanent license or a different temporary license, then the timer halts. The timer only starts again when you reactivate the temporary license.
• If the temporary license is active, and you shut down the ASA, then the timer continues to count down. If you intend to leave the ASA in a shut down state for an extended period of time, then you should activate the permanent license before you shut down to preserve the temporary license. • When a temporary license expires, the next time you reload the ASA, the permanent license is used; you are not forced to perform a reload immediately when the license expires. Note We suggest you do not change the system clock after you install the temporary license. If you set the clock to be a later date, then if you reload, the ASA checks the system clock against the original installation time, and assumes that more time has passed than has actually been used. If you set the clock back, and the actual running time is greater than the time between the original installation time and the system clock, then the license immediately expires after a reload. How Multiple Licenses Interact • When you activate a temporary license, then features from both permanent and temporary licenses are merged to form the running license.
Note that the ASA only uses the highest value from each license for each feature; the values are not added together. The ASA displays any resolved conflicts between the licenses when you enter a temporary activation key.
In the rare circumstance that a temporary license has lower capability than the permanent license, the permanent license values are used. • When you activate a permanent license, it overwrites the currently-running permanent and temporary licenses and becomes the running license.
Note If you install a new permanent license, and it is a downgrade from the temporary license, then you need to reload the ASA to disable the temporary license and restore the permanent license. Until you reload, the temporary license continues to count down. If you reactivate the already installed permanent license, you do not need to reload the ASA; the temporary license does not continue to count down, and there is no disruption of traffic. • To reenable the features of the temporary license if you later activate a permanent license, simply reenter the temporary activation key. For a license upgrade, you do not need to reload.
• To switch to a different temporary license, enter the new activation key; the new license is used instead of the old temporary license and combines with the permanent license to create a new running license. The ASA can have multiple temporary licenses installed; but only one is active at any given time. See the following figure for examples of permanent and VPN Flex activation keys, and how they interact. Figure 3-1 Permanent and VPN Flex Activation Keys 1.
In example 1 in the above figure, you apply a temporary key with 25 SSL sessions; because the VPN Flex value is greater than the permanent key value of 10 sessions, the resulting running key is a merged key that uses the VPN Flex value of 25 sessions, and not a combined total of 35 sessions. In example 2 above, the merged key from example 1 is replaced by the permanent key, and the VPN Flex license is disabled. The running key defaults to the permanent key value of 10 sessions.
In example 3 above, an evaluation license including 50 contexts is applied to the permanent key, so the resulting running key is a merged key that includes all the features of the permanent key plus the 50 context license. In example 4 above, the merged key from example 3 has the VPN Flex key applied.
Because the ASA can only use one temporary key at a time, the VPN flex key replaces the evaluation key, so the end result is the same as the merged key from example 1. Failover and Temporary Licenses With failover, identical licenses are required. For failover purposes, temporary and permanent licenses appear to be identical, so you can have a permanent license on one unit and a temporary license on the other unit. This functionality is useful in an emergency situation; for example, if one of your units fails, and you have an extra unit, you can install the extra unit while the other one is repaired. If you do not normally use the extra unit for SSL VPN, then a VPN Flex license is a perfect solution while the other unit is being repaired. Because the temporary license continues to count down for as long as it is activated on a failover unit, we do not recommend using a temporary license in a permanent failover installation; when the temporary license expires, failover will no longer work.
Shared Licenses A shared license lets you purchase a large number of SSL VPN sessions and share the sessions as needed amongst a group of ASAs by configuring one of the ASAs as a shared licensing server, and the rest as shared licensing participants. This section describes how a shared license works, and includes the following topics: • • • • • Information About the Shared Licensing Server and Participants The following steps describe how shared licenses operate: 1. Decide which ASA should be the shared licensing server, and purchase the shared licensing server license using that device serial number. Decide which ASAs should be shared licensing participants, including the shared licensing backup server, and obtain a shared licensing participant license for each device, using each device serial number. (Optional) Designate a second ASA as a shared licensing backup server. You can only specify one backup server. Note The shared licensing backup server only needs a participant license.
Configure a shared secret on the shared licensing server; any participants with the shared secret can use the shared license. When you configure the ASA as a participant, it registers with the shared licensing server by sending information about itself, including the local license and model information. Note The participant needs to be able to communicate with the server over the IP network; it does not have to be on the same subnet. The shared licensing server responds with information about how often the participant should poll the server. When a participant uses up the sessions of the local license, it sends a request to the shared licensing server for additional sessions in 50-session increments. The shared licensing server responds with a shared license. The total sessions used by a participant cannot exceed the maximum sessions for the platform model.
Note The shared licensing server can also participate in the shared license pool. It does not need a participant license as well as the server license to participate. If there are not enough sessions left in the shared license pool for the participant, then the server responds with as many sessions as available.
The participant continues to send refresh messages requesting more sessions until the server can adequately fulfill the request. When the load is reduced on a participant, it sends a message to the server to release the shared sessions.
Note The ASA uses SSL between the server and participant to encrypt all communications. Communication Issues Between Participant and Server See the following guidelines for communication issues between the participant and server: • If a participant fails to send a refresh after 3 times the refresh interval, then the server releases the sessions back into the shared license pool. • If the participant cannot reach the license server to send the refresh, then the participant can continue to use the shared license it received from the server for up to 24 hours. • If the participant is still not able to communicate with a license server after 24 hours, then the participant releases the shared license, even if it still needs the sessions. The participant leaves existing connections established, but cannot accept new connections beyond the license limit. • If a participant reconnects with the server before 24 hours expires, but after the server expired the participant sessions, then the participant needs to send a new request for the sessions; the server responds with as many sessions as can be reassigned to that participant. Information About the Shared Licensing Backup Server The shared licensing backup server must register successfully with the main shared licensing server before it can take on the backup role.
When it registers, the main shared licensing server syncs server settings as well as the shared license information with the backup, including a list of registered participants and the current license usage. The main server and backup server sync the data at 10 second intervals. After the initial sync, the backup server can successfully perform backup duties, even after a reload. When the main server goes down, the backup server takes over server operation. The backup server can operate for up to 30 continuous days, after which the backup server stops issuing sessions to participants, and existing sessions time out. Be sure to reinstate the main server within that 30-day period. Critical-level syslog messages are sent at 15 days, and again at 30 days.
When the main server comes back up, it syncs with the backup server, and then takes over server operation. When the backup server is not active, it acts as a regular participant of the main shared licensing server.
Note When you first launch the main shared licensing server, the backup server can only operate independently for 5 days. The operational limit increases day-by-day, until 30 days is reached. Also, if the main server later goes down for any length of time, the backup server operational limit decrements day-by-day. When the main server comes back up, the backup server starts to increment again day-by-day. For example, if the main server is down for 20 days, with the backup server active during that time, then the backup server will only have a 10-day limit left over. The backup server 'recharges' up to the maximum 30 days after 20 more days as an inactive backup. This recharging function is implemented to discourage misuse of the shared license.
Failover and Shared Licenses This section describes how shared licenses interact with failover, and includes the following topics: • • Failover and Shared License Servers This section describes how the main server and backup server interact with failover. Because the shared licensing server is also performing normal duties as the ASA, including performing functions such as being a VPN gateway and firewall, then you might need to configure failover for the main and backup shared licensing servers for increased reliability.
Note The backup server mechanism is separate from, but compatible with, failover. Shared licenses are supported only in single context mode, so Active/Active failover is not supported.
Both main shared licensing server units in the failover pair need to have the same license. So if you purchase a 10,000 session shared license for the primary main server unit, you must also purchase a 10,000 session shared license for the standby main server unit. Because the standby unit does not pass traffic when it is in a standby state, the total number of sessions remains at 10,000 in this example, not a combined 20,000 sessions. For Active/Standby failover, the primary unit acts as the main shared licensing server, and the standby unit acts as the main shared licensing server after failover; because both units need to have the same license, both units can act as the main licensing server.
The standby unit does not act as the backup shared licensing server. Instead, you can have a second pair of units acting as the backup server, if desired. For example, you have a network with 2 failover pairs. Pair #1 includes the main licensing server. Pair #2 includes the backup server.
When the primary unit from Pair #1 goes down, the standby unit immediately becomes the new main licensing server. The backup server from Pair #2 never gets used. Only if both units in Pair #1 go down does the backup server in Pair #2 come into use as the shared licensing server. If Pair #1 remains down, and the primary unit in Pair #2 goes down, then the standby unit in Pair #2 comes into use as the shared licensing server (see ). Figure 3-2 Failover and Shared License Servers The standby backup server shares the same operating limits as the primary backup server; if the standby unit becomes active, it continues counting down where the primary unit left off. See the for more information.
Failover and Shared License Participants For participant pairs, both units register with the shared licensing server using separate participant IDs. The active unit syncs its participant ID with the standby unit. The standby unit uses this ID to generate a transfer request when it switches to the active role. This transfer request is used to move the shared sessions from the previously active unit to the new active unit. Maximum Number of Participants The ASA does not limit the number of participants for the shared license; however, a very large shared network could potentially affect the performance on the licensing server. In this case, you can increase the delay between participant refreshes, or you can create two shared networks.
Licenses FAQ Q. Can I activate multiple temporary licenses, for example, VPN Flex and Botnet Traffic Filter? You can only use one temporary license at a time. The last license you activate is the one in use. In the case of evaluation licenses that group multiple features into one activation key, then multiple features are supported at the same time. But temporary licenses for sale by Cisco are limited to one feature per activation key.
Can I 'stack' temporary licenses so that when the time limit runs out, it will automatically use the next license? You can install multiple temporary licenses, but only the last activated license is active. When the active license expires, you need to manually activate the new one. Be sure to activate it shortly before the old one expires so you do not lose functionality. (Any remaining time on the old license remains unused; for example, if you use 10 months of a 12-month license, and activate a new 12-month license, then the remaining 2 months of the first license goes unused unless you later reactivate it. We recommend that you activate the new license as close as possible to the end of the old license to maximize the license usage.) Q. Can I install a new permanent license while maintaining an active temporary license?
The temporary license will be deactivated when you apply a permanent license. You have to activate the permanent license, and then reactivate the temporary license to be able to use the new permanent license along with the temporary license. This will cause temporary loss of functionality for the features reliant on the temporary license. For failover, can I use a shared licensing server as the primary unit, and the shared licensing backup server as the secondary unit? The secondary unit must also have a shared licensing server license.
The backup server, which has a participant license, can be in a separate failover pair of two backup servers. Do I need to buy the same licenses for the secondary unit in a failover pair? Even for a shared licensing server? Both units need the same licenses.
For a shared licensing server, you need to buy the same shared licensing server license for both units. Note: In Active/Standby failover, for licenses that specify the number of sessions, the sessions for both units are not added to each other; only the active unit sessions can be used. For example, for a shared SSL VPN license, you need to purchase a 10,000 user session for both the active and the standby unit; the total number of sessions is 10,000, not 20,000 combined. Can I use a VPN Flex or permanent SSL VPN license in addition to a shared SSL VPN license? The shared license is used only after the sessions from the locally installed license (VPN Flex or permanent) are used up.
Note: On the shared licensing server, the permanent SSL VPN license is not used; you can however use a VPN Flex license at the same time as the shared licensing server license. In this case, the VPN Flex license sessions are available for local SSL VPN sessions only; they cannot be added to the shared licensing pool for use by participants. Guidelines and Limitations See the following guidelines for activation keys. Context Mode Guidelines • In multiple context mode, apply the activation key in the system execution space.
• Shared licenses are not supported in multiple context mode. Firewall Mode Guidelines All license types are available in both routed and transparent mode. Failover Guidelines • You must have the same licenses activated on the primary and secondary units.
Note For failover purposes, there is no distinction between permanent and temporary licenses as long as the feature set is the same between the two units. See the for more information. • Shared licenses are not supported in Active/Active mode. See the for more information. Upgrade Guidelines Your activation key remains compatible if you upgrade to Version 8.2 or later, and also if you later downgrade. After you upgrade, if you activate additional feature licenses that were introduced before 8.2, then the activation key continues to be compatible with earlier versions if you downgrade.
However if you activate feature licenses that were introduced in 8.2 or later, then the activation key is not backwards compatible. If you have an incompatible license key, then see the following guidelines: • If you previously entered an activation key in an earlier version, then the ASA uses that key (without any of the new licenses you activated in Version 8.2 or later). • If you have a new system and do not have an earlier activation key, then you need to request a new activation key compatible with the earlier version. Additional Guidelines and Limitations • The activation key is not stored in your configuration file; it is stored as a hidden file in Flash memory.
• The activation key is tied to the serial number of the device. Feature licenses cannot be transferred between devices (except in the case of a hardware failure). If you have to replace your device due to a hardware failure and it is covered with Cisco TAC, contact the Cisco Licensing Team to have your existing license transferred to the new serial number. The Cisco Licensing Team will ask for the Product Authorization Key reference number and existing serial number.
• Once purchased, you cannot return a license for a refund or for an upgraded license. • You cannot add two separate licenses for the same feature together; for example, if you purchase a 25-session SSL VPN license, and later purchase a 50-session license, you cannot use 75 sessions; you can use a maximum of 50 sessions. (You may be able to purchase a larger license at an upgrade price, for example from 25 sessions to 75 sessions; this kind of upgrade should be distinguished from adding two separate licenses together). • Although you can activate all license types, some features are incompatible with each other; for example, multiple context mode and VPN.
In the case of the AnyConnect Essentials license, the license is incompatible with the following licenses: full SSL VPN license, shared SSL VPN license, and Advanced Endpoint Assessment license. By default, the AnyConnect Essentials license is used instead of the above licenses, but you can disable the AnyConnect Essentials license in the configuration to restore use of the other licenses using the no anyconnect-essentials command. Viewing Your Current License This section describes how to view your current license, and for temporary activation keys, how much time the license has left.
Detailed Steps Command Purpose show activation-key detail Example: hostname# show activation-key detail Shows the installed licenses, including information about temporary licenses.